Safeguard Your Third-Party Ecosystem from Emerging Threats
When new threats and vulnerabilities emerge, your Third-Party Risk Management (TPRM) team needs to act fast. Any interruption or breach in your service supply chain could have a lasting negative impact on your business. It’s a tough task, as many TPRM teams are underequipped to handle the:
- Exponential growth in the number of vulnerability alerts: Which alerts are relevant to your organization? Who monitors them?
- Sheer volume of your third (and fourth) parties: Which vendors could be prone to each threat?
- Workload required to assess the extended vendor ecosystem against each threat: Do we have to assess every service provider?
- Post-incident reporting required by executive leadership: How can we quickly summarize our actions and remedies?
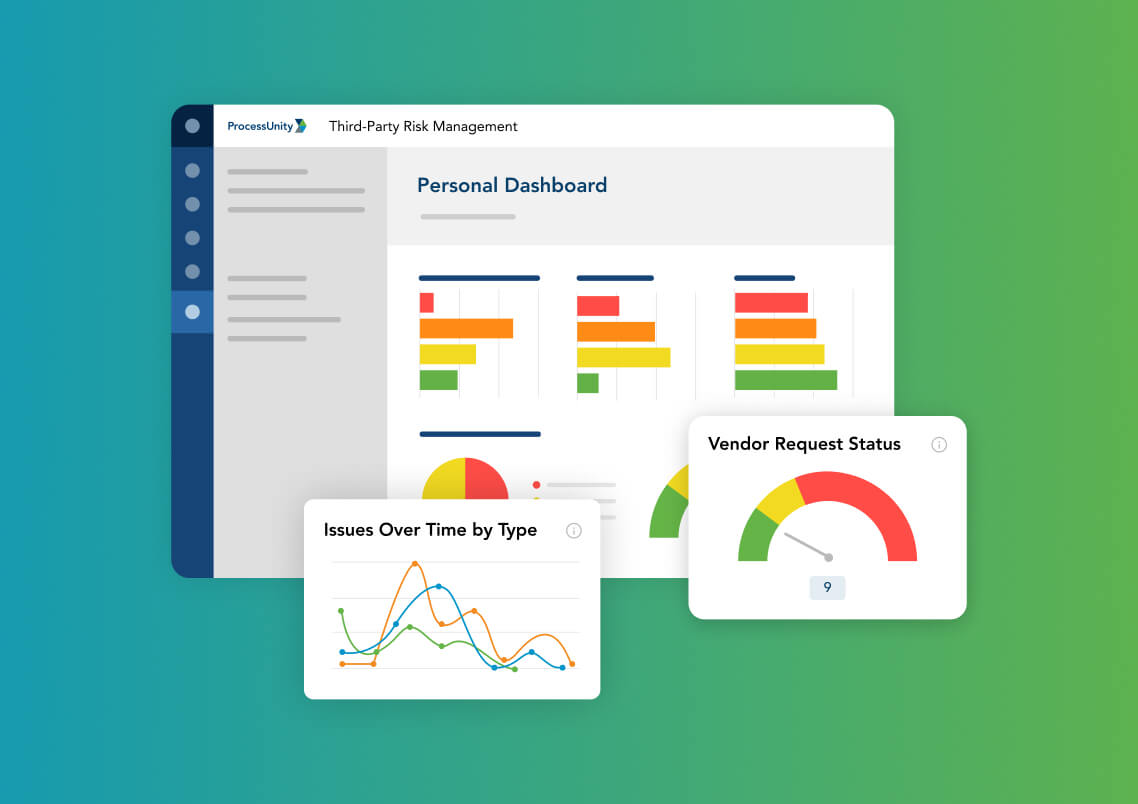
Threat & Vulnerability Response Highlights
Access a searchable list of real-time vulnerabilities with metadata on the CVSS score, severity, attack vector attack complexity, affected platforms, and more.
Set risk rules and alerts to continuously monitor your critical third parties against vulnerabilities that match your pre-set criteria.
Narrow your list of third parties to assess using filters for inherent risk, framework score, alert severity, and more.
Streamline assessment reviews with configurable preferred responses and questionnaire scoring.
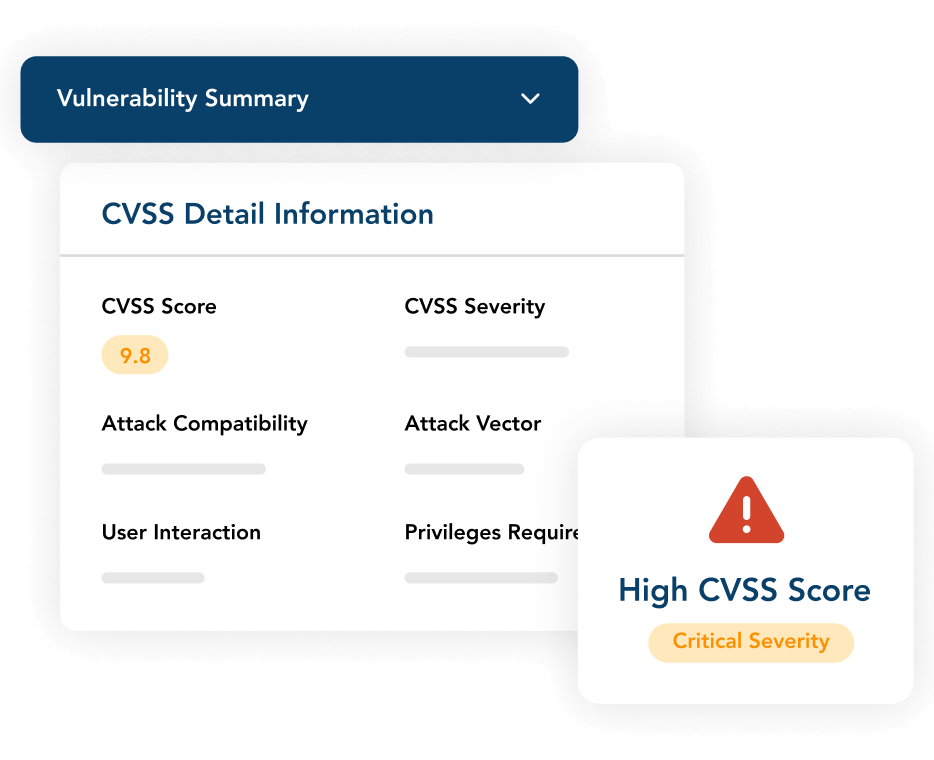



Why ProcessUnity Threat & Vulnerability Response?
Streamlining Third-Party Risk Mitigation
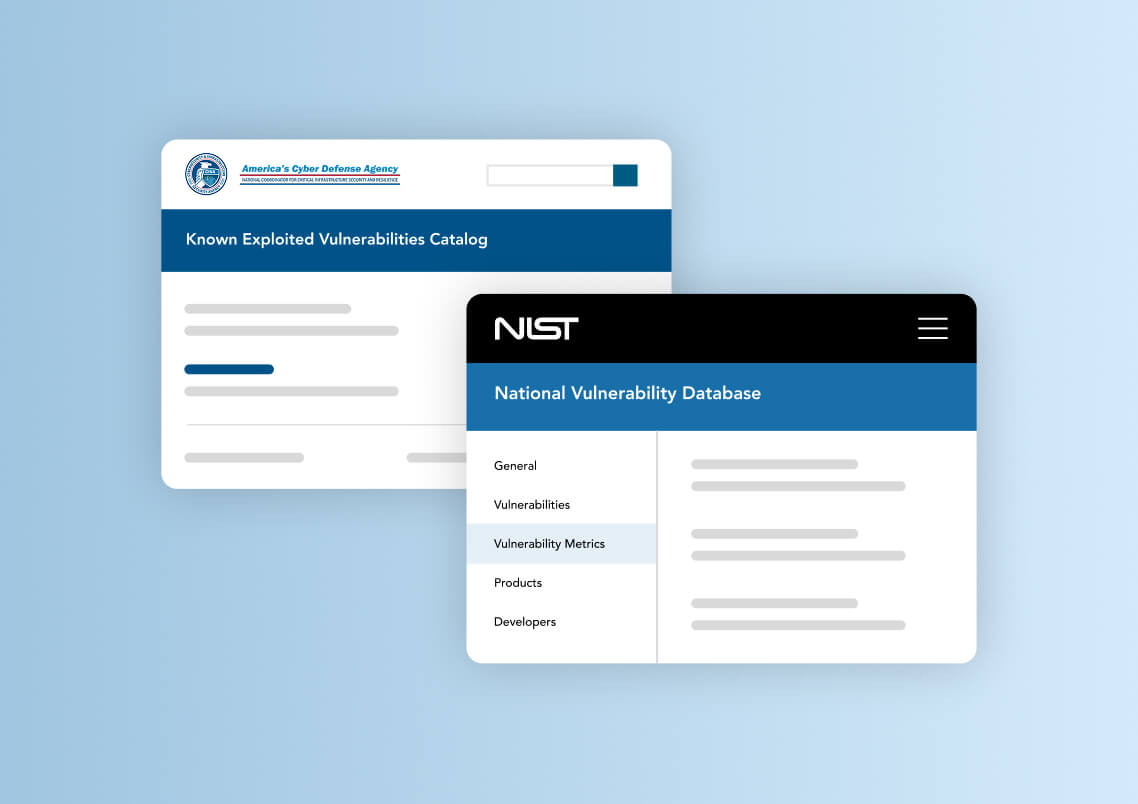
Continuous Threat Monitoring and Alerts
The ProcessUnity Threat Research team continuously monitors CISA’s Known Exploited Vulnerabilities Catalog and NIST’s National Vulnerability Database for published vulnerabilities. In conjunction, our team conducts ongoing threat intelligence research into the dark web, social media, and indicators of compromise to identify emerging threats relevant to your organization. If one or more of your third parties is susceptible to an emerging threat, an alert is issued with key details necessary for you to understand its nature.
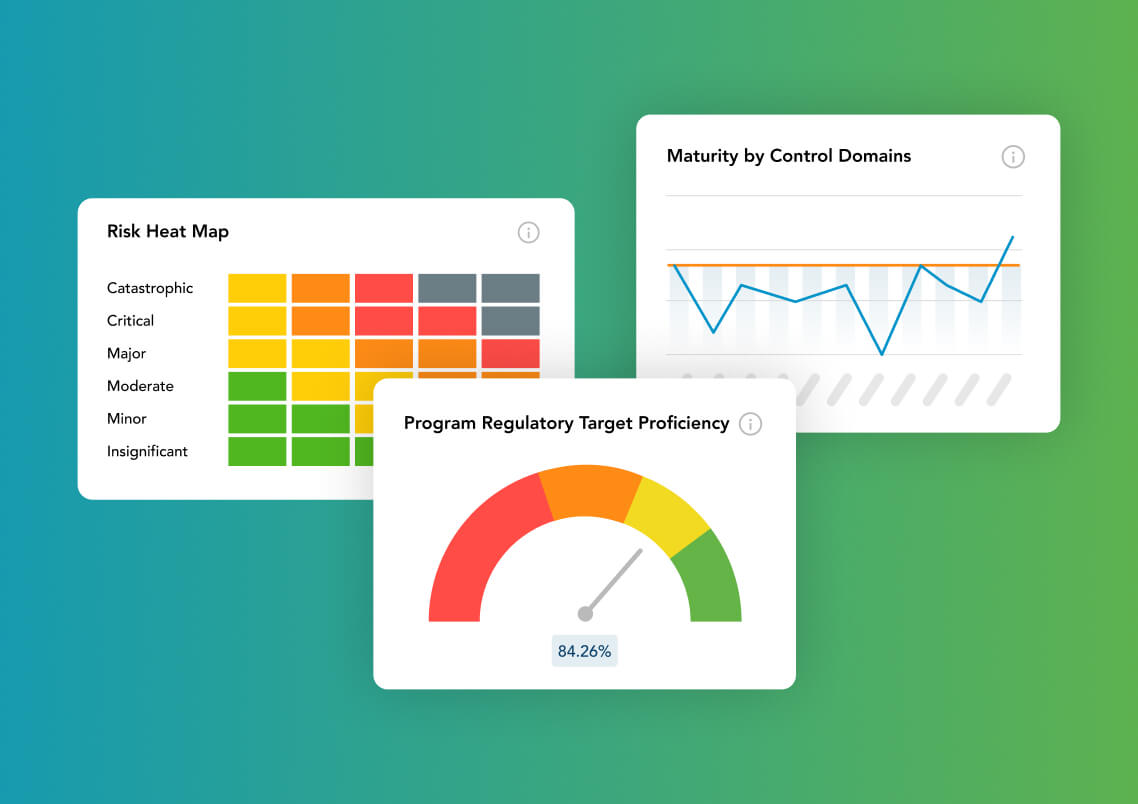
Assessment Prioritization
When a threat is identified, ProcessUnity combines inherent risk assessments, Automated Risk Profiles, potential control deficiencies, and demographic and technographic data to deliver a narrowed list of third parties most likely to be susceptible to the threat. Instead of assessing your entire ecosystem, you focus on the vendors that matter most, streamlining your threat and vulnerability assessment process.
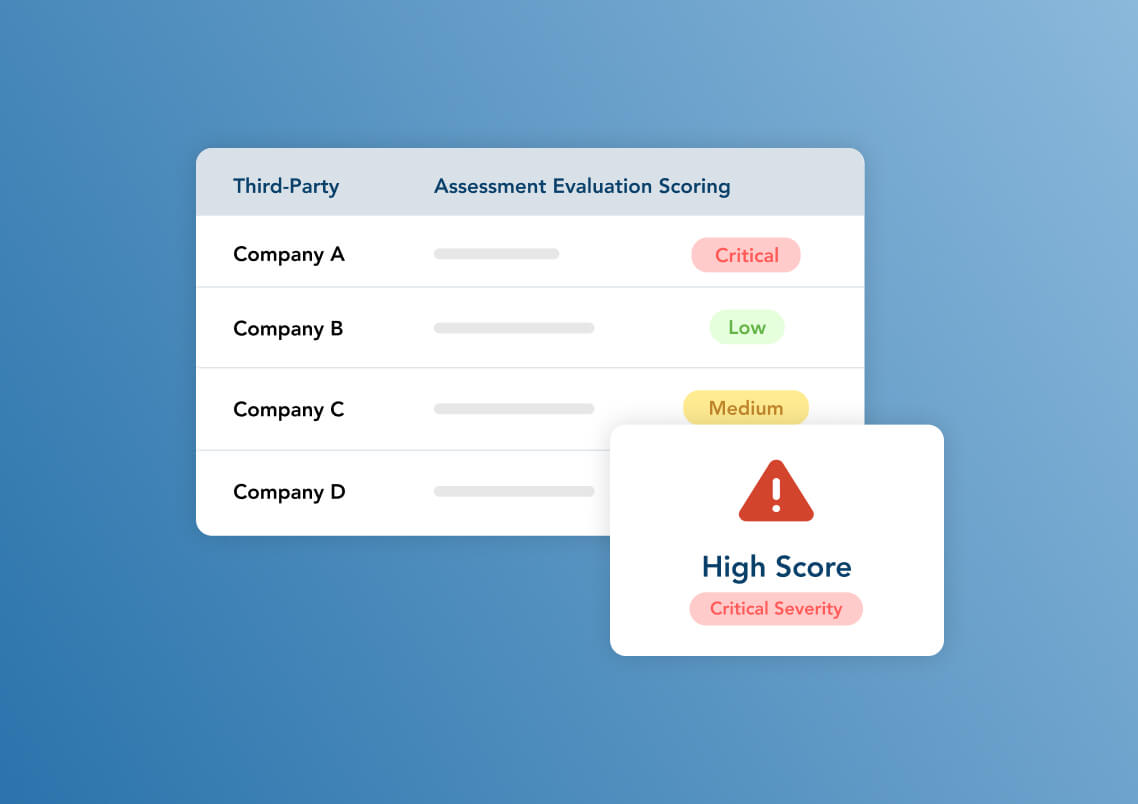
Assessment Scoping and Scoring
Potentially affected third and fourth parties receive targeted assessments via ProcessUnity’s powerful assessment engine and our flexible vendor portal. Assessment questions automatically incorporate threat metadata, such as the name of the affected application and NIST CVE ID, promoting a faster response. As your vendors complete their assessment, ProcessUnity automatically scores the results based on preferred responses that you determine. The platform automatically creates issues for remediation based on non-preferred responses.
One-Click Executive Reporting
Often, the anxiety and frustration of senior executives and the board during a critical crisis can be mollified with transparency. This is especially true during an active cyber threat. ProcessUnity Threat and Vulnerability Management Software provides summary reports to educate your leadership on assessment status. With the push of a button, you can generate a report demonstrating the effectiveness of your process, showcasing your leadership and your team’s efficiency during an active cyber threat crisis.
Calculate Your Potential Savings
with ProcessUnity
Build a business case to uplevel your Third-Party Risk Management program. Answer a few short questions and generate your custom savings report.
Calculate Your ROI Now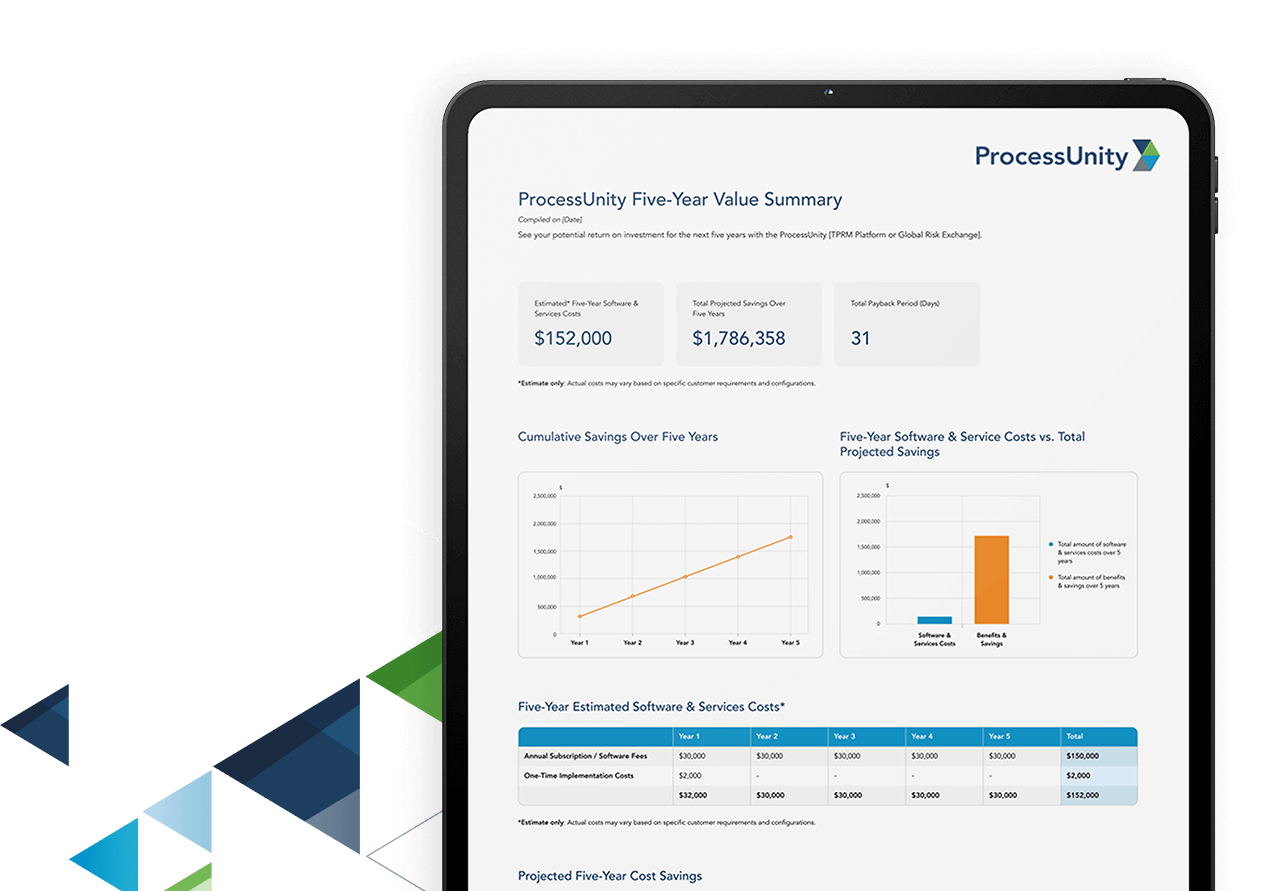
Frequently Asked Questions
Threat and vulnerability management is the proactive process of identifying, assessing, and mitigating security risks from potential threats and emerging vulnerabilities across your third-party ecosystem.
A vulnerability is a weakness in your systems, like outdated software or poor configurations. A threat is an active danger, such as hackers or malware, that seeks to exploit those weaknesses.
To identify, assess, and respond to emerging cybersecurity threats effectively:
- Identify threats early using real-time threat intelligence and AI-powered monitoring tools, as well as actively scan external databases for new vulnerabilities as they’re discovered.
- Assess which of your business-critical third parties are most vulnerable to those threats when they emerge.
- Respond with targeted remediation measures and communicate results to key stakeholders.
A threat and vulnerability management software helps streamline this process for more effective, AI-powered third-party risk management.
A threat and vulnerability assessment identifies exploitable weaknesses and evaluates exposure to active threats, helping organizations prioritize remediation across their third-party network.
ProcessUnity Threat & Vulnerability Response integrates seamlessly with SIEM and Vulnerability Management tools, enhancing — not replacing — your current security stack. This creates a unified risk management framework, eliminating blind spots and enabling a comprehensive approach to vulnerability response.
Request a Demo:
ProcessUnity's Threat and Vulnerability
Management Software
Our team is here to show you how forward-thinking organizations are elevating their
Third-Party Risk Management programs and practices to maximize risk reduction. Start
your journey with ProcessUnity today.





