Eliminate Time-Consuming Vendor Evidence Reviews
Validating third-party controls requires your team to review volumes of vendor-submitted evidence that accompanies questionnaire responses. It’s an extremely important process, yet it’s rife with inefficiency and inconsistency that ultimately slows vendor onboarding and significantly contributes to assessment backlog. With too many vendors, even more evidence to review, and never enough resources, how can your team keep pace without sacrificing quality? The answer is artificial intelligence.
ProcessUnity Evidence Evaluator: AI-Based Third-Party Controls Validation
Enhance the speed and precision of your onboarding and post-contract due diligence processes with Evidence Evaluator. An integral component of the ProcessUnity TPRM Platform, Evidence Evaluator employs Natural Language Processing (NLP) and Generative AI to instantly review attestations, certifications, policies, procedures, and other information security artifacts to automatically validate third-party controls. In seconds, Evidence Evaluator highlights potential security gaps, eliminating the need to manually review documentation.
Trained using the world’s most comprehensive Third-Party Risk Management Large Language Model (LLM), Evidence Evaluator can read and understand virtually any document submitted as part of the vendor assessment process. Examples include:
- Statement of Controls Reports (SOC 1, SOC 2, etc.)
- Certifications (ISO27001, etc.)
- Completed Questionnaires (SIG Core, SIG Light, etc.)
- Compliance Attestations (GDPR, CCPA, etc.)
- Information Security Policies & Procedures
- Business Continuity / Disaster Recovery Plans
ProcessUnity’s AI parses the documentation and instantly confirms or refutes vendor questionnaire responses, highlighting where in the specific documents it found the information to make its determination.

Webinar
Introducing ProcessUnity GenAI: Evidence Evaluator

Whitepaper
Accelerate Third-Party Policy Reviews with AI
Uncover Risks Faster with Purpose-Built AI Tools
Auto-Complete Questionnaires
Use Evidence Evaluator to complete your questionnaire automatically, drastically reducing vendor response time. Ask your third party to submit their information security documentation and Evidence Evaluator will answer the questions based on their submitted material. You then have the option to send the completed questionnaire to your third party for review or only send the questions that couldn’t be answered due to lack of evidence. Either way, you significantly reduce vendor response time and speed up your evaluation.
Accelerate Third-Party Reviews
Evidence Evaluator reviews supporting evidence faster than the humans on your team, shortening the assessment review cycle and freeing your analysts to focus on risk remediation instead of information inspection. If you’re outsourcing policy and document reviews, Evidence Evaluator will help you reduce unneeded spend and refocus it on other third-party risk tasks.
Surface Unseen Risk in Assessment Evidence
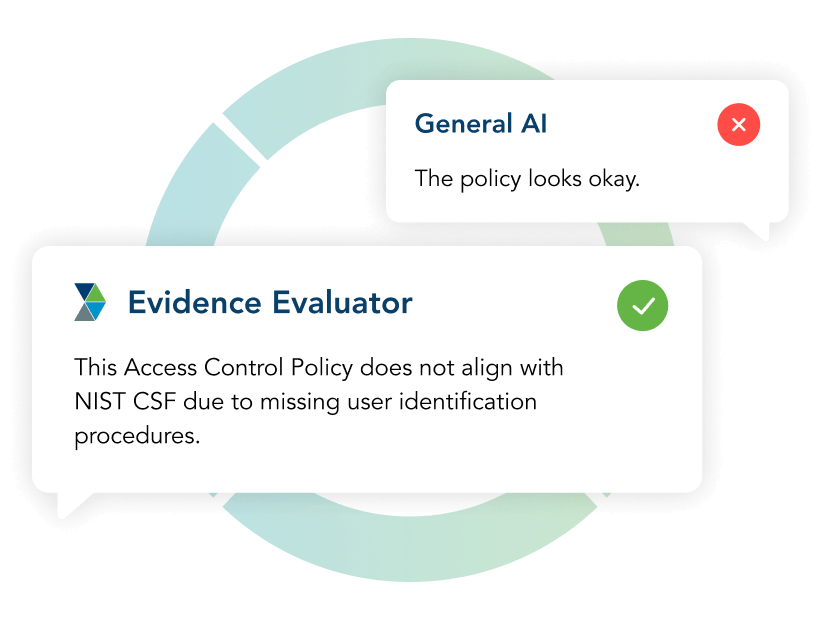
Evidence Evaluator helps you establish uniformity and accuracy in evidence reviews, ensuring critical information is not overlooked or interpreted differently by your individual analysts. The AI-driven technology automatically retrains itself to evolving standards, constantly tuning its ability to recognize the nuances between evolving frameworks.
Whether your program follows NIST, ISO, CIS, or a custom control set, Evidence Evaluator identifies and extracts the right information, aligns it to your program’s requirements, and delivers structured, assessment-ready insights in an instant. The days of manually mapping results to your framework are over.
Trust the Results
Unlike similar tools that rely on public or general-purpose AI, Evidence Evaluator is trained using ProcessUnity’s unparalleled TPRM Large Language Model, comprised of tens of thousands of completed assessments and hundreds of thousands of vendor profiles. As a result, our output is accurate, context-aware, and highly relevant to the specific risk types that analysts work with every day.
The technology is also private by design, with all data encrypted in transit and at rest, and automatically discarded after processing. There’s no risk of vendor evidence being retained, reused, or exposed to third-party models. This means security teams can confidently use ProcessUnity to scale their reviews, knowing our model understands the nuance of cybersecurity and keeps their data and third parties’ data safe.
Our Platform Solutions
Automate the complete third-party risk lifecycle, from initial onboarding to ongoing monitoring, with the industry’s most configurable workflow platform.
Learn MoreAccess the industry’s most extensive network of pre-validated vendor assessments and real-time risk intelligence. Our exchange platform enables organizations to make faster, more informed decisions using shared risk data, eliminating redundant assessments and providing deeper insights into potential vulnerabilities across your vendor ecosystem.
Learn MoreFrequently Asked Questions
AI-based third-party control reviews automate the validation of third-party controls by using advanced AI — including natural language processing (NLP) and generative models — to analyze third-party evidence (such as policies, certifications, and attestations) in real time. This enhances both the speed and accuracy of due diligence processes, and greatly reduces the internal resources needed to conduct evidence review.
AI analyzes third-party controls in seconds — reducing review timelines from months to minutes. The platform automatically analyzes and validates large volumes of third-party evidence and provides resulting decisions in seconds, including specific locations where evidence was identified, helping to streamline third-party risk assessments at scale.
AI improves the accuracy of third-party controls validation by leveraging a purpose-built language model trained for third-party risk management. These models are trained to interpret and assess control documentation with high consistency, reducing human error and ensuring objective, data-driven validation outcomes.
Yes. AI-based third-party control reviews support audit readiness by providing:
- Version-controlled risk logs
- Centralized due diligence repositories
- Automated workflows with built-in approval paths
This approach ensures every risk decision is fully documented and traceable, simplifying audit preparation.
AI-based third-party reviews protect sensitive third-party data through strict encryption both in transit and at rest. Data is never stored permanently — it’s processed automatically and disposed of after use, ensuring full compliance with data protection and privacy regulations.
Next Steps:
Schedule a ProcessUnity Platform Demo
Our team is here to show you how forward-thinking organizations are elevating
their Third-Party Risk Management programs and practices to maximize risk
reduction. Start your journey with ProcessUnity today.