End-to-End Third-Party Risk Management
Organizations of all sizes and program maturity turn to ProcessUnity to overcome their toughest Third-Party Risk
Management challenges. How can we help you improve your program?
See How ProcessUnity Transforms TPRM
Watch the video to learn how our solutions help you:
- Automate TPRM processes
- Accelerate vendor onboarding and due diligence
- Extend third-party portfolio coverage
- Empower your team with purpose-built AI
- Systematically close your TPRM vulnerability gap
Powerful, Innovative TPRM Platforms
ProcessUnity combines innovative technologies with industry best practices and unparalleled expertise to
mature third-party risk and cybersecurity risk management programs.
Third-Party Risk Management
Automate critical third-party risk management processes from sourcing and onboarding, through post-contract due diligence, vendor service reviews and eventual offboarding. Mature your program with our award-winning platform that powers the world’s top TPRM programs.
Explore Now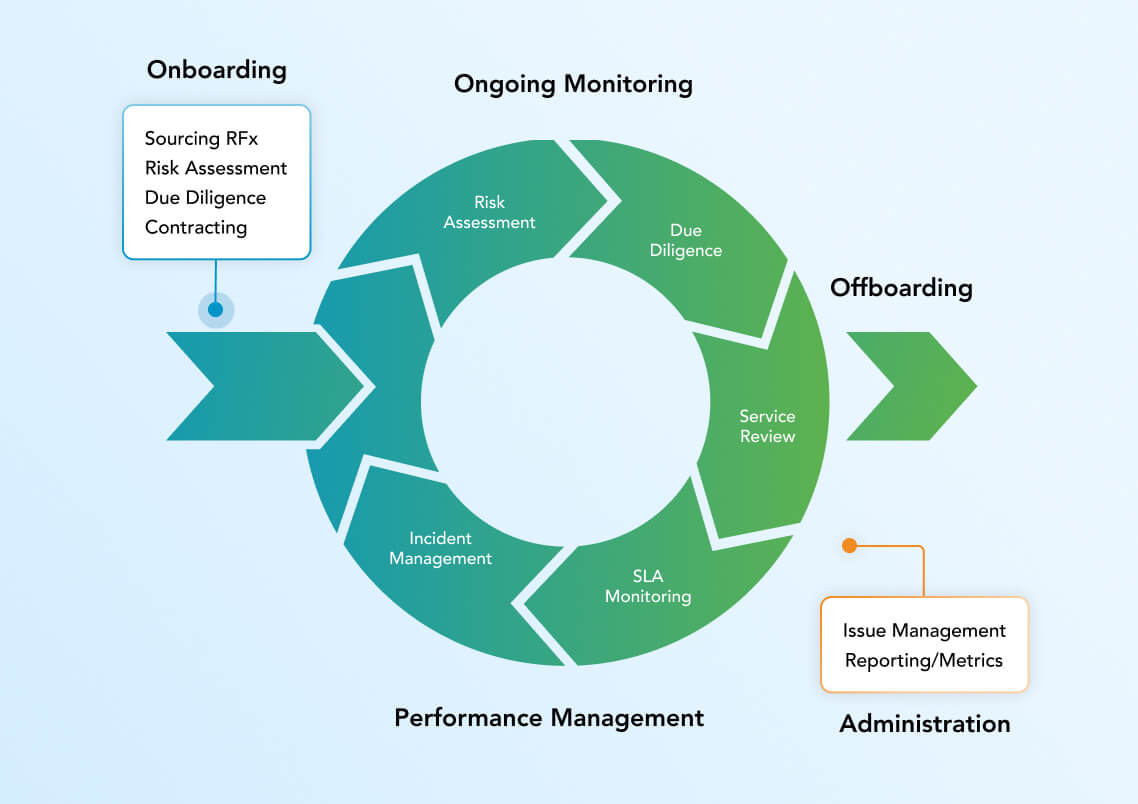
Global Risk Exchange
With 18,000 completed assessments and more than 370,000 curated vendor risk profiles, ProcessUnity’s Global Risk Exchange significantly reduces assessment workloads and extends your team to cover 100% of your vendor ecosystem.
Explore Now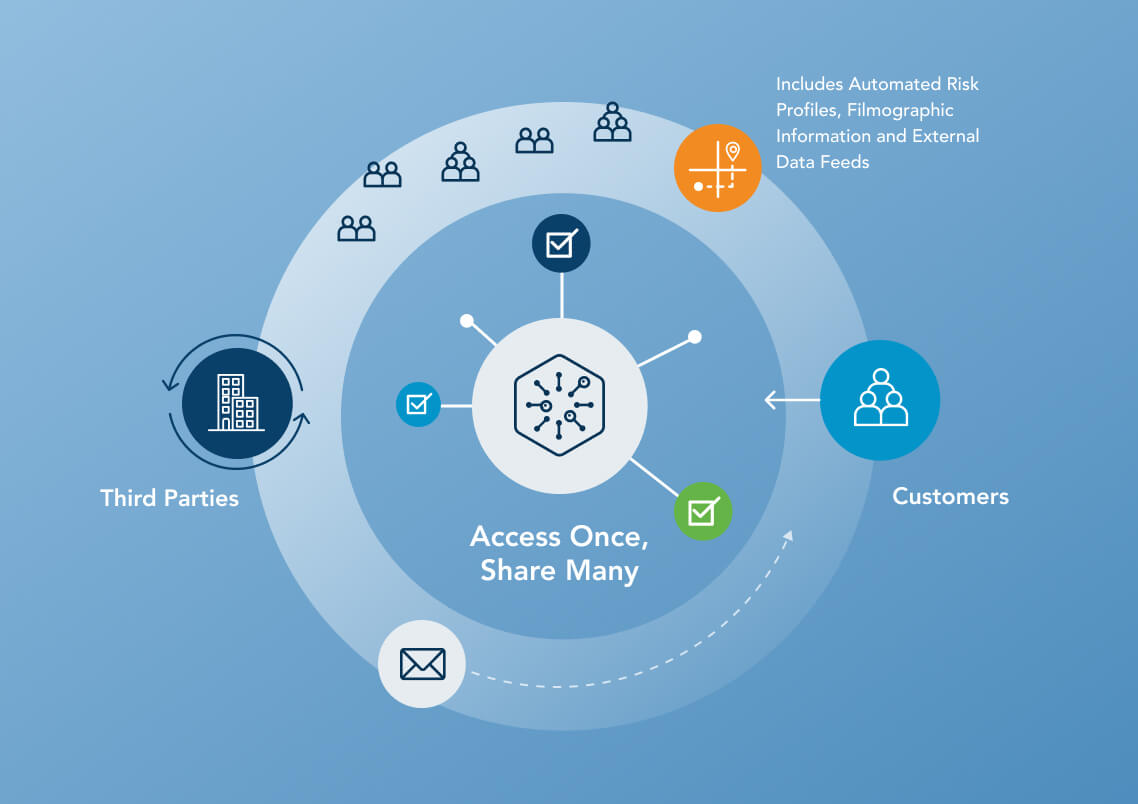
Threat & Vulnerability Response
Identify when threats and vulnerabilities emerge and quickly gauge your third-party ecosystem for susceptibility via a four-step vendor prioritization and assessment process. Reduce your response time from weeks or months to a few short days.
Explore Now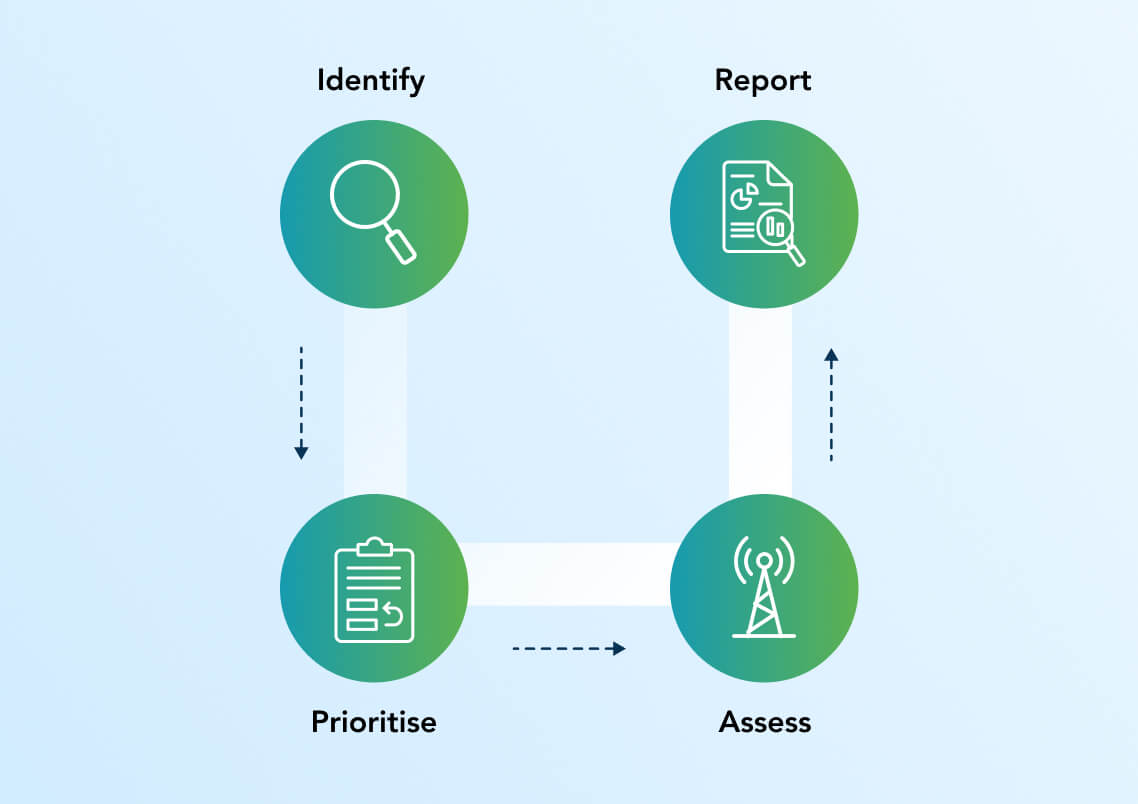
Cybersecurity Risk Management
Prove cyber readiness with a single platform to monitor cyber risks, improve mitigating controls and prioritize program activities. Powered by automation, ProcessUnity creates a defensible cybersecurity risk management program that bolsters organizational resilience.
Explore Now
Calculate Your Potential Savings with ProcessUnity
Build a business case to uplevel your Third-Party Risk Management program. Answer a few short questions and generate your custom savings report.
Calculate Your ROI Now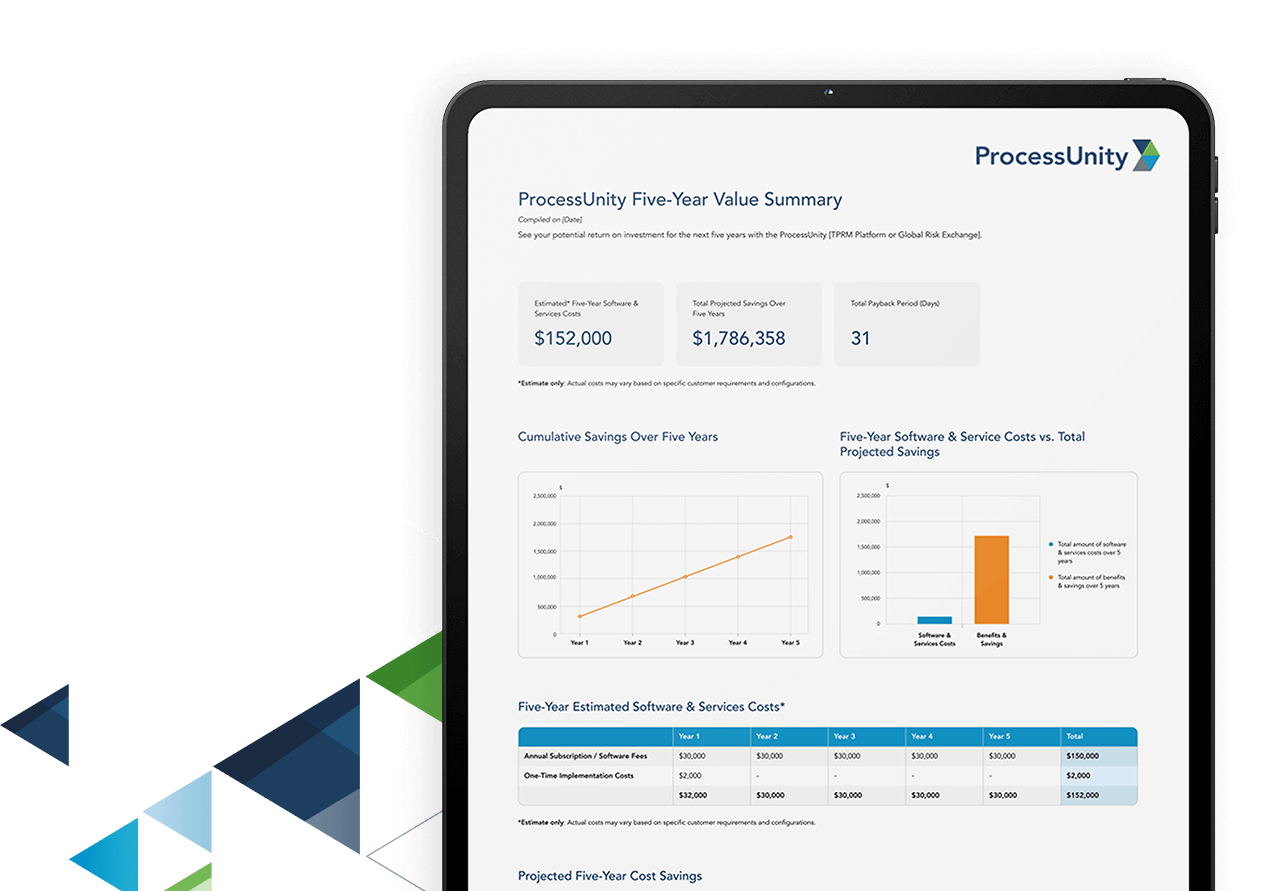
See How ProcessUnity Can Help Today.
Request a DemoProcessUnity: Modern, Effective
Third-Party Risk Management
ProcessUnity customers gain significant return on their investment via measurable improvement gains.
*Read the ProcessUnity Value Perspective from GRC 20/20 for more
details on how we maximize customer return on investment.
Get Started with ProcessUnity Today
Request a demo to uplevel your program and get Third-Party Risk Management done right.
Request a DemoCalculate Your
Potential Savings with Our ROI Calculator





