Third parties can introduce substantial risk into global supply networks, but rigorous vendor risk assessments can be costly and time-consuming to complete. By adopting a data-first approach, you can simplify and optimize your vendor onboarding, without compromising the quality of risk screening and due diligence.
- Find out how ProcessUnity and LSEG work together to deliver trusted data for vendor assessment purposes and help simplify the process of conducting due diligence of vendors during onboarding.
- Learn how adopting a data-first approach can help you simplify and optimize your vendor onboarding, without compromising the quality of risk screening and due diligence.
The changing environment around vendor risk assessment
Against a backdrop of rising fraud, bribery, corruption and other forms of financial crime, corporate organizations are acutely aware of the potential risk that third parties can introduce into global supply networks.
A strict regulatory environment, combined with the threat of potential reputational damage if responsible business practices are not ensured throughout third-party networks means that robust third-party risk assessments combined with screening and monitoring are critical for organizational success.
Furthermore, risk professionals are increasingly aware of the need to conduct multi-faceted risk assessments investigating a range of potential risks. For example, it is no longer enough to assess information security or cyber risk alone. Organizations need to fully assess, monitor and manage a range of potential third-party risks, including environmental, social and governance (ESG), integrity, identity, operational, financial, reputational risks, and more. Companies are increasingly expected to adopt a sophisticated risk-based approach to compliance because of the strict-liability nature of most sanctions’ regimes. The risks associated with sanctioned entities and individuals are often hidden due to complex supply chain networks and ownership structures. In a backdrop of geopolitical tensions, it is paramount for organizations to have access to trusted, accurate and comprehensive screening data, a key pillar of a robust compliance program.
When assessing vendor risk, this need for a multi-faceted approach translates into lengthier, more complicated onboarding processes, usually including detailed questionnaires, which can create vendor and analyst fatigue and place undue pressure on often scarce resources.
The challenge of collecting the right data
Screening has a pivotal role to play in all aspects of third-party risk management (TPRM). The right screening datasets can help risk and compliance teams build a holistic picture of potential risk, more easily identify relationships where heightened risk may be present, spot trends, pinpoint concerns, and more.
That said, collecting the data directly from your third parties is not always a straightforward task. This can impact the veracity of the entire risk assessment process, because without complete and trusted data, effective risk assessment is impossible.
Looking specifically at risk assessments in the vendor onboarding space, gathering robust and complete data for each vendor can quickly become a substantial challenge. Vendor provided data may not be objective, in part because vendors may not provide an accurate or complete picture of their risk profile. Responses can also be incomplete if vendors simply don’t respond to requests for information at all. Repeated requests for information can become time-consuming, costly and slow the pace of business – but, more than this, they can create negative experiences that damage key vendor relationships.
Reducing your risk assessment burden
ProcessUnity has partnered with LSEG’s flagship risk intelligence database World-Check to address these data and scalability challenges and deliver a solution that reduces the vendor assessment burden by adopting a data-first approach. This allows customers to screen third parties and their beneficial owners (individuals and organizations) against the World-Check database and use the Media Check screening tool to further support their due diligence needs in the fight against financial crime, bribery, and corruption. The data provided simplifies compliance with regulatory obligations relating to anti-bribery anti-corruption (ABAC), enabling detailed screening and monitoring of politically exposed persons (PEPs) and heightened risk individuals and entities.
Our combined capabilities deliver trusted data for vendor assessment purposes and simplify the process of conducting due diligence of vendors during onboarding. In this way we help to empower TPRM teams to complete vendor assessments faster and gain greater coverage across their vendor portfolio. ProcessUnity also uses data from additional sources including the Global Risk Exchange and flags the potential discrepancies in vendor responses for you, so teams spend less time chasing and validating vendor identity and ultimate beneficial ownership (UBO) data.
It’s worth noting that data can be incorporated into a variety of TPRM use-cases, including procurement due diligence (determining which vendors to contract from a shortlist), onboarding, ongoing monitoring, and more. ProcessUnity offers a variety of complete, proven third-party risk program workflows developed to facilitate ongoing monitoring needs throughout the entire vendor lifecycle, and integrates with World-Check screening to help customers mitigate risk and continuously assess vendors more efficiently. Companies using the combined offering can support bribery and corruption risk management as a part of their TPRM program.
When assessments run smoothly, questions aren’t duplicated, and vendors aren’t repeatedly asked the same questions they’ve already answered. Additionally, teams can ensure a happy, stable vendor relationship, and mitigate the potential inheritance of third-party risk in the process.
This partnership is just one example of using a data-first approach, supplemented by leading technology, to simplify risk management in an environment that is increasingly complex and demanding – and to remain on the right side of an evolving regulatory risk curve without slowing the pace of business.
—
To dive deeper into the unified approach provided by the ProcessUnity workflow and World-Check database, please visit our webpage: https://www.processunity.com/vendor-screening-intelligence-lseg-risk-intelligence/
Related Articles

Cut Risk, Not Corners: Streamlining the...
The modern organization relies on a larger, more integrated network of third parties and suppliers..
Learn More
Accelerate Control Reviews with ProcessUnity’s Evidence...
Third-party risk assessments are becoming increasingly complex and resource-intensive. Manual evidence reviews create bottlenecks, inconsistent..
Learn More
5 Cybersecurity Frameworks Financial Institutions Can’t...
Regulatory pressure is intensifying — and financial institutions are feeling the heat. In 2024, the..
Learn More
ProcessUnity Evidence Evaluator: AI-Based Third-Party Controls...
See how ProcessUnity’s GenAI-powered feature simplifies third-party risk assessments. In just 60 seconds, discover how..
Learn More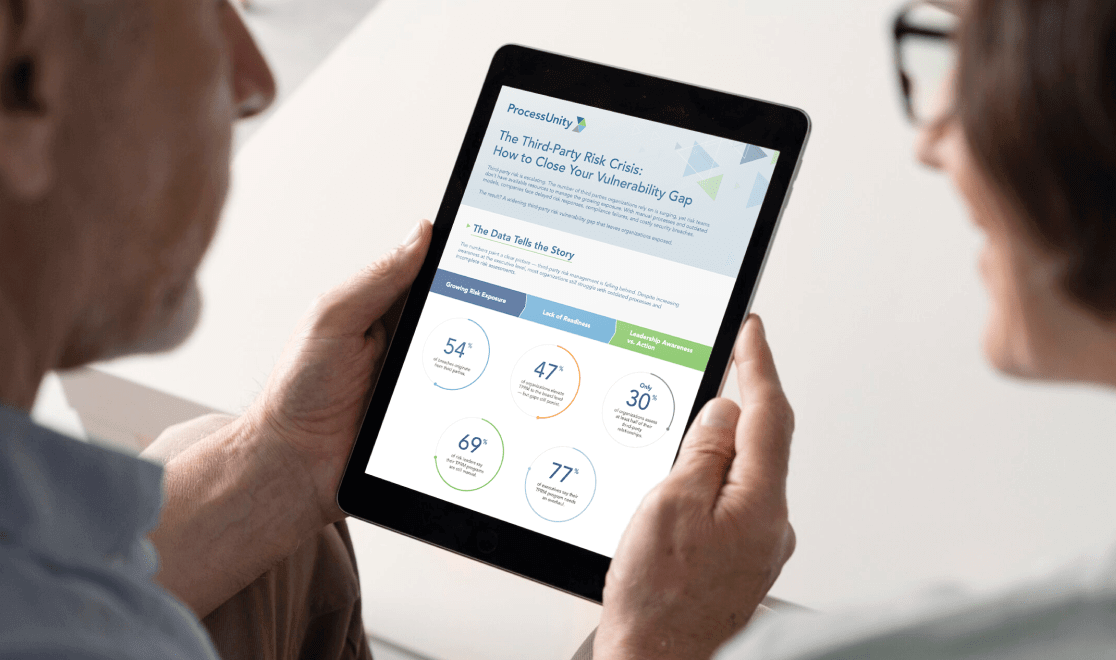
How to Close Your Third-Party Risk...
Is your organization exposed to hidden third-party risks that could create dangerous blind spots in..
Learn More
8 Ways Your Business Benefits from...
Cyber threats are intensifying. Regulatory scrutiny is increasing. Legacy assessments simply can’t keep pace. To..
Learn More
5 Critical Regulations Reshaping TPRM in...
The pressure on financial institutions to manage third-party risk is mounting — and the stakes..
Learn More
How Third-Party Vendor Risk Disrupts Business...
Your third-party vendors are delivering on time, business operations are efficient and planned, and customers..
Learn More
10 Critical Third-Party Risk Management Challenges...
Every vendor relationship can introduce potential vulnerabilities to your business, and in today's hyperconnected business..
Learn More
Ensure Ongoing DORA Compliance Across Your...
The Digital Operational Resilience Act (DORA) is a regulatory framework established by the European Union..
Learn More
5 Essential Steps to Modernize Your...
Third-party relationships have become a critical vulnerability point - with 54% of security breaches occurring..
Learn More
ProcessUnity Introduces a Revolutionary Platform to...
Threat and Vulnerability Response Platform Utilizes Proprietary Threat Intelligence to Rapidly Identify Third-party Gaps and..
Learn More
Revolutionizing Response to Emerging Third-Party Cybersecurity...
Introducing ProcessUnity’s New Threat and Vulnerability Response Platform to Quickly Identify Emerging Threats and Assess..
Learn More
How Organizations and Vendors Use a...
A third-party risk exchange is a transformative concept designed to make third-party risk management (TPRM)..
Learn More
ProcessUnity Introduces Industry’s All-In-One Third-Party Risk...
Completes Integration with Global Risk Exchange; Augments Resources to Extend Coverage to More Outsourced Service..
Learn More
Mature Your Cyber Program with a...
Risk-based cybersecurity risk management is the process of identifying, tracking and mitigating the risks to..
Learn More
Controls-Based Versus Risk-Based Cybersecurity Programs
In the face of an escalating regulatory burden and increasingly common data breaches, many teams..
Learn More
Manage Cybersecurity Risk with the SCF...
The Secure Controls Framework (SCF) Risk Management Model can be a powerful tool for teams..
Learn More
Optimize Vendor Onboarding by Aligning with...
During the vendor onboarding process, both cybersecurity and procurement manage the amount of risk brought..
Learn More
3 Takeaways about Anti-Bribery and Corruption...
Anti-bribery and corruption programs grant businesses visibility into their internal practices and third-party networks to..
Learn More
Properly Scoping Vendor Due Diligence Drives...
Properly Scoping Vendor Due Diligence Saves Both Time and Money One of the costliest mistakes..
Learn More
Security Assessments 2.0: The Next Generation...
The more things change, the more they stay the same. It's a well-worn adage that..
Learn More
How to Conduct Third-Party Due Diligence
Identifying and engaging with the right partners is essential to the success of most businesses...
Learn More
Evaluating Security Risk When Onboarding New...
In today’s tightly interwoven supply chains and highly competitive markets, organizations must continuously evaluate and..
Learn More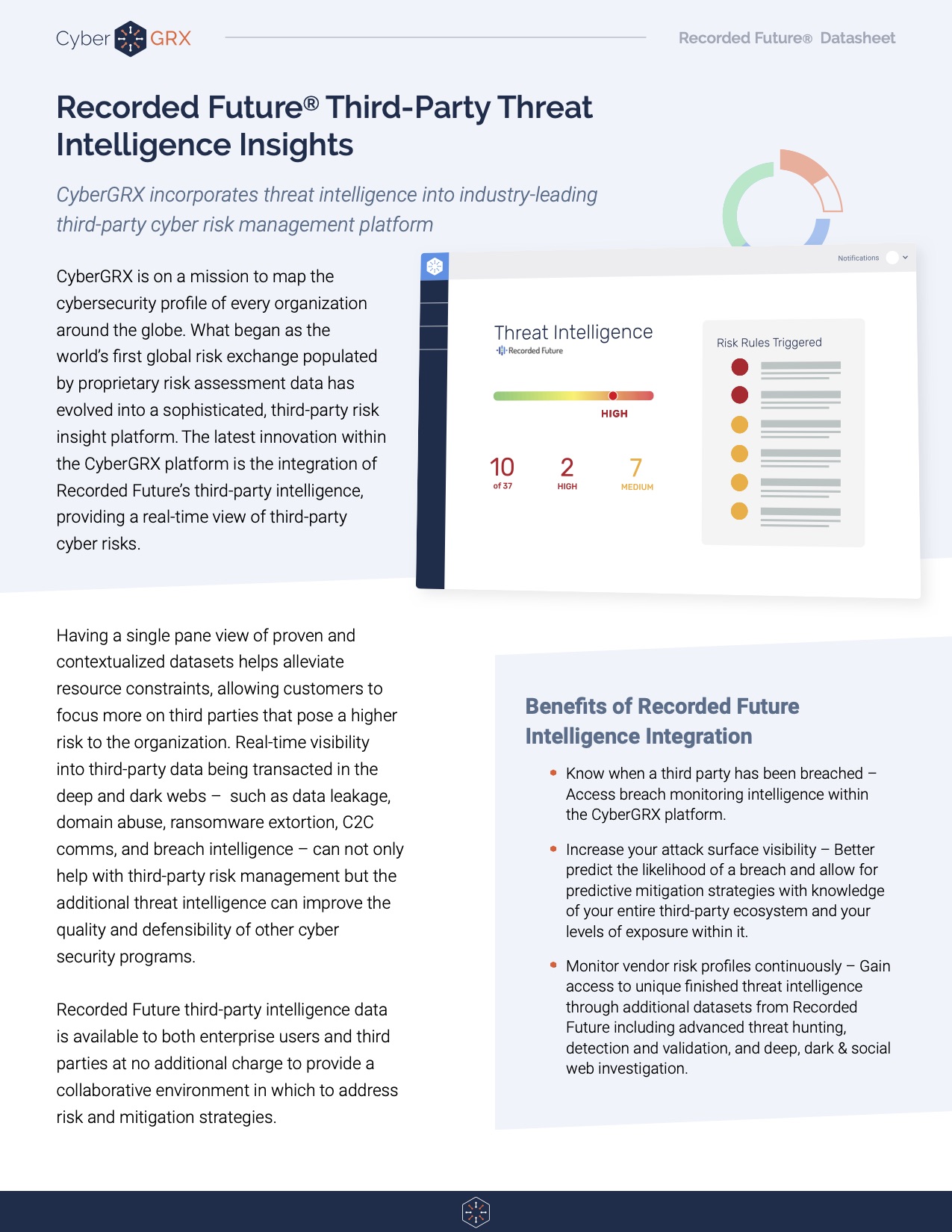
Recorded Future Third-Party Threat Intelligence Insights
Having a single pane view of proven and contextualized datasets helps alleviate resource constraints, allowing..
Learn More
5 Areas to Mitigate Risk in...
If you work within a Vendor Risk Management (VRM) team, you know that third-party risk..
Learn More
5 Tips to Improve Your Vendor...
Vendor due diligence is essential to any third-party risk management program. However, no two due diligence processes are..
Learn More
Inherent Risk vs. Residual Risk in...
Conducting a thorough vendor risk analysis is an integral step in Vendor Risk Management. However,..
Learn More
What is Third-Party Risk Management?
Third-Party Risk Management is the process of identifying, managing and mitigating risks present in a vendor relationship. This..
Learn More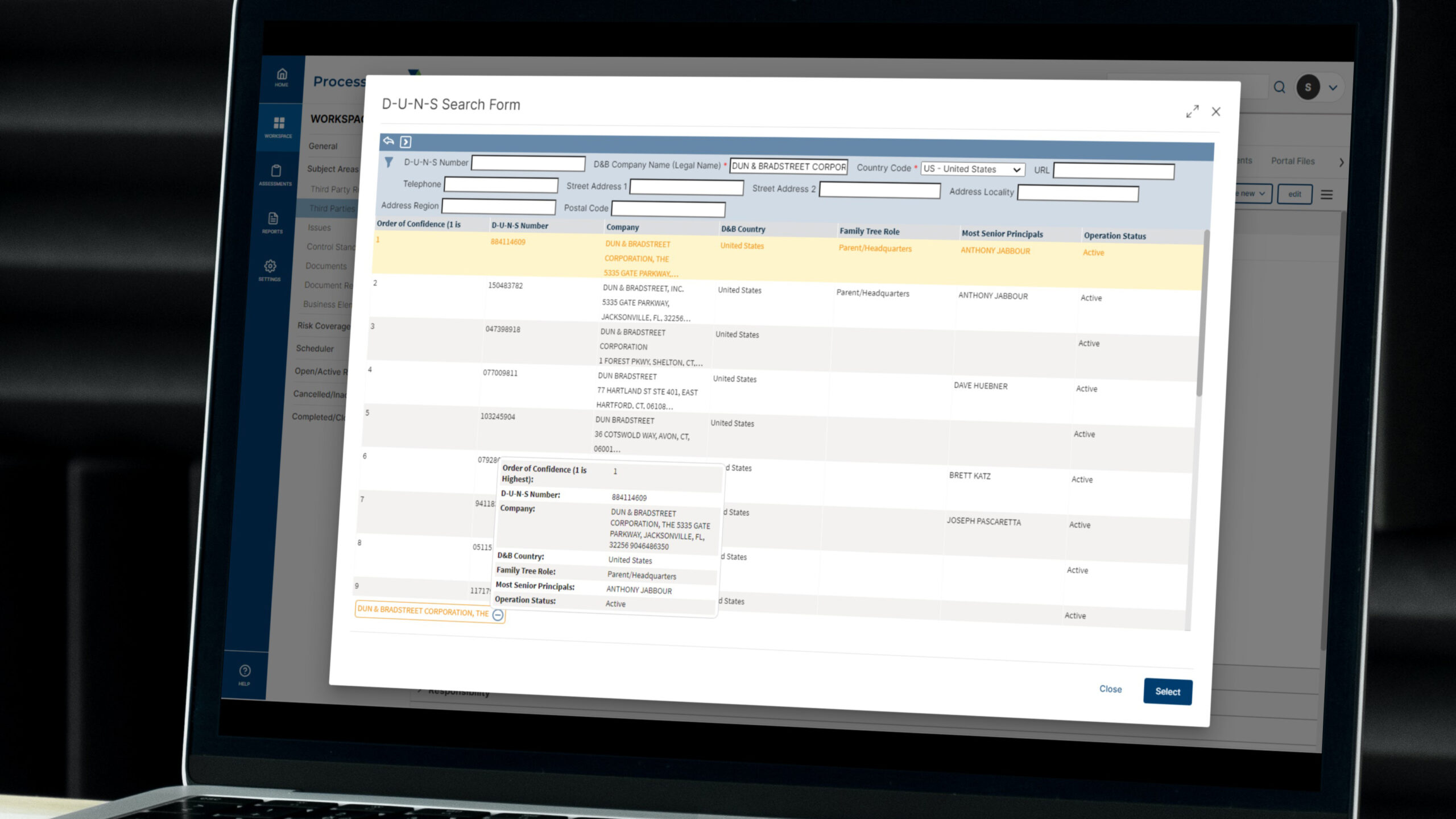
ProcessUnity Vendor Identity Intelligence with Dun...
ProcessUnity Vendor Identity Intelligence seamlessly and automatically incorporates D&B’s D-U-N-S Search and Beneficial Owner Search..
Learn More
Anti-Bribery & Corruption (ABAC) in Business...
The impacts of corruption can be very severe and have been historically well documented. On a political level, corruption – however and wherever..
Learn More
What Is Third-Party Risk Management: The...
The recent SolarWinds breach has reminded news organizations, businesses, and leadership teams around the world..
Learn More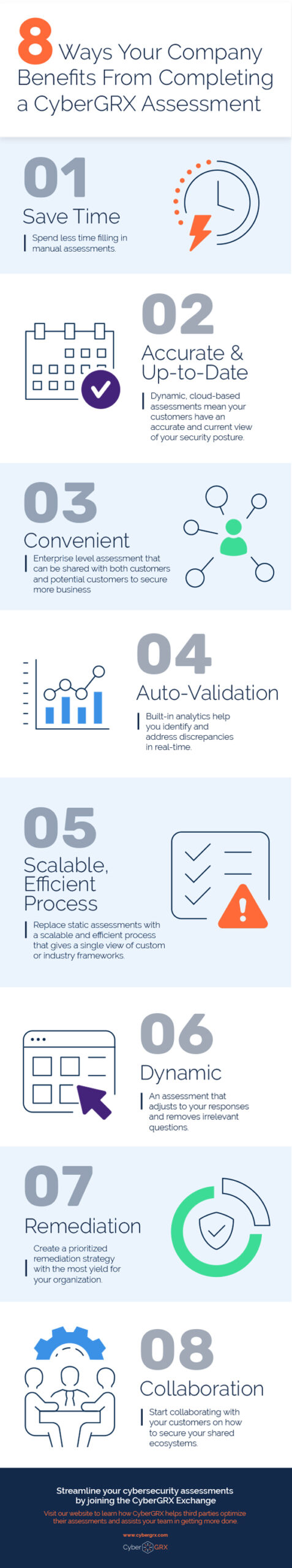
8 Benefits of Completing a CyberGRX...
CyberGRX modernizes and streamlines redundant and inefficient processes that come with shared and static..
Learn More
Third-Party Risk Management Best Practices
New Guide Offers Expert Advice for Effective and Efficient Vendor-Risk Processes A robust, effective, and..
Learn More
Best Practice Program for ProcessUnity Vendor...
ProcessUnity Vendor Risk Management (VRM) protects companies and their brands by reducing risks from third-party vendors and..
Learn More
ProcessUnity Vendor Financial Intelligence Powered By...
ProcessUnity Vendor Financial Intelligence (VFI) with RapidRatings seamlessly incorporates RapidRatings’ financial health ratings into ProcessUnity’s Third-Party..
Learn More
Vendor Screening Intelligence with Refinitiv
ProcessUnity Vendor Screening Intelligence (VSI) embeds LSEG World-Check One’s third-party screening capabilities into ProcessUnity’s Third-Party Risk..
Learn More
How to Stay Ahead of Risk...
Managing risk through pre-contract vendor due diligence in a digitally connected world Thanks to increasing..
Learn MoreAbout Us
ProcessUnity is a leading provider of cloud-based applications for risk and compliance management. The company’s software as a service (SaaS) platform gives organizations the control to assess, measure, and mitigate risk and to ensure the optimal performance of key business processes. ProcessUnity’s flagship solution, ProcessUnity Vendor Risk Management, protects companies and their brands by reducing risks from third-party vendors and suppliers. ProcessUnity helps customers effectively and efficiently assess and monitor both new and existing vendors – from initial due diligence and onboarding through termination. Headquartered outside of Boston, Massachusetts, ProcessUnity is used by the world’s leading financial service firms and commercial enterprises. For more information, visit www.processunity.com.