How Third-Party Vendor Risk Disrupts Business Continuity, and What to Do About It
4 minute read
April 2025
Your third-party vendors are delivering on time, business operations are efficient and planned, and customers are satisfied. Then, without warning, a third-party disruption brings everything to a halt.
Everything’s Running Smoothly — Until It’s Not
What started as a potentially minor issue, one only involving your third party, can quickly spiral into a full-scale crisis — without immediate remediation or a vulnerability response plan in place, your supply chain can collapse, sensitive data can be exposed, and previously unknown compliance violations can surface. The financial and reputational damage is swift and severe.
This isn’t a far-fetched scenario, it’s the cost of overlooking third-party vendor risk — a real and growing threat that organizations must manage proactively. The key? A robust, data-backed third-party risk management (TPRM) strategy.
The Domino Effect: How One Third-Party Failure Can Grow to Disrupt Entire Industries
Third-party failures are rarely isolated incidents. In today’s interconnected economy, a single failure can set off a chain reaction across industries — impacting businesses far beyond the initial point of failure.
Take the July 2024 CrowdStrike incident for example. A faulty software update triggered a global IT outage, affecting 8.5 million Windows devices. Airlines grounded flights, retailers couldn’t process payments, and hospitals had to postpone non-urgent care.
The estimated financial impact? Over $1 billion.
This wasn’t just an IT mishap — it was a wake-up call for organizations everywhere: unchecked third-party risk can compromise even the most resilient businesses.
Common Third-Party Vendor Risks You Can’t Afford to Leave Unchecked
Third-party vendor risk often hides in plain sight — until it’s too late. Here are the most common risks to monitor for — and the impact they can have if left to spread:
- Cybersecurity weaknesses
Your security is only as strong as your weakest third party. Even organizations with strong internal cybersecurity defenses can be compromised by a third party with poor controls. A single weak link can lead to extensive data breaches, service outages, and regulatory penalties throughout your business environment. - Compliance gaps
Third parties must meet ever-evolving regulatory requirements. If they fall short — especially when handling sensitive data — your organization could face fines, legal action, and reputational damage. - Operational inefficiencies
Underperforming third parties create delays, quality issues, and service interruptions. These inefficiencies damage customer satisfaction and hurt your bottom line. - Outdated vulnerability response practices
Time-consuming manual processes create dangerous security blind spots, delay remediation efforts, and drain valuable resources that could be allocated more strategically. - Financial instability
Third parties facing financial distress may be forced to cut corners and reduce service capabilities, including reduce the resources spent on cyber risk assessments and protection. In some cases, third parties can go out of business entirely, leaving you scrambling for replacements.
Breaking the Chain: How to Proactively Manage Third-Party Vendor Risk
Third-party vendor risks are inevitable, but business disruptions don’t have to be. A proactive TPRM approach helps you get ahead of issues before they escalate. Here’s how to build resilience and proactively manage risk in your third-party network:
- Diversify vendors and build contingency plans
Avoid over-reliance on a single vendor for critical services. Build a diversified third-party portfolio and develop clear contingency plans to minimize disruption if a key third party falters.
Leverage a centralized TPRM platform like ProcessUnity to manage your vendor risk efficiently, gain full visibility into your third-party portfolio, streamline assessment cycles, address risks quickly, and activate remediation plans when necessary. - Standardize and automate risk assessments
Before onboarding, evaluate each third party’s cybersecurity maturity, compliance track record, financial stability, and operational resilience.
ProcessUnity makes it easy to standardize and automate these assessments — ensuring consistency, saving time, and reducing blind spots. Tap into a third-party risk exchange for pre-vetted assessments and insights on hard-to-assess third parties. - Implement continuous monitoring, not point-in-time assessments
Risk doesn’t pause once a contract is signed. Continuous monitoring uncovers real-time changes in vendor posture — from financial red flags to new compliance exposures.
A robust TPRM solution empowers you to detect, respond to, and resolve issues faster with always-on visibility and real-time alerts. - Use AI to prioritize and predict risk
As your third-party ecosystem grows, the volume of data you need to manage increases exponentially. Manual methods fall short in covering your full portfolio of third parties.
With ProcessUnity’s AI-powered analytics, you can identify patterns and trends, detect anomalies, and prioritize high-impact risks — all while freeing your team from low-value tasks and redundant processes to focus on critical threats.
Future-Proof Your Business with Resilient Third-Party Vendor Risk Management
Third-party vendor risk is a business reality. But with the right tools and approach, you can transform it from a reactive burden into a proactive strategy for resilience.
ProcessUnity empowers organizations to stay ahead of third-party threats by integrating automation, AI, and real-time risk intelligence into a single, centralized platform.
With better visibility, streamlined assessments, and continuous monitoring, you can make smarter decisions, respond faster to emerging risks, and build a more agile, secure vendor ecosystem.
Ready to transform your third-party risk management program?
See how ProcessUnity can help you strengthen resilience and stay one step ahead of disruption. Request a demo today.
Related Articles

Cut Risk, Not Corners: Streamlining the...
The modern organization relies on a larger, more integrated network of third parties and suppliers..
Learn More
Accelerate Control Reviews with ProcessUnity’s Evidence...
Third-party risk assessments are becoming increasingly complex and resource-intensive. Manual evidence reviews create bottlenecks, inconsistent..
Learn More
5 Cybersecurity Frameworks Financial Institutions Can’t...
Regulatory pressure is intensifying — and financial institutions are feeling the heat. In 2024, the..
Learn More
ProcessUnity Evidence Evaluator: AI-Based Third-Party Controls...
See how ProcessUnity’s GenAI-powered feature simplifies third-party risk assessments. In just 60 seconds, discover how..
Learn More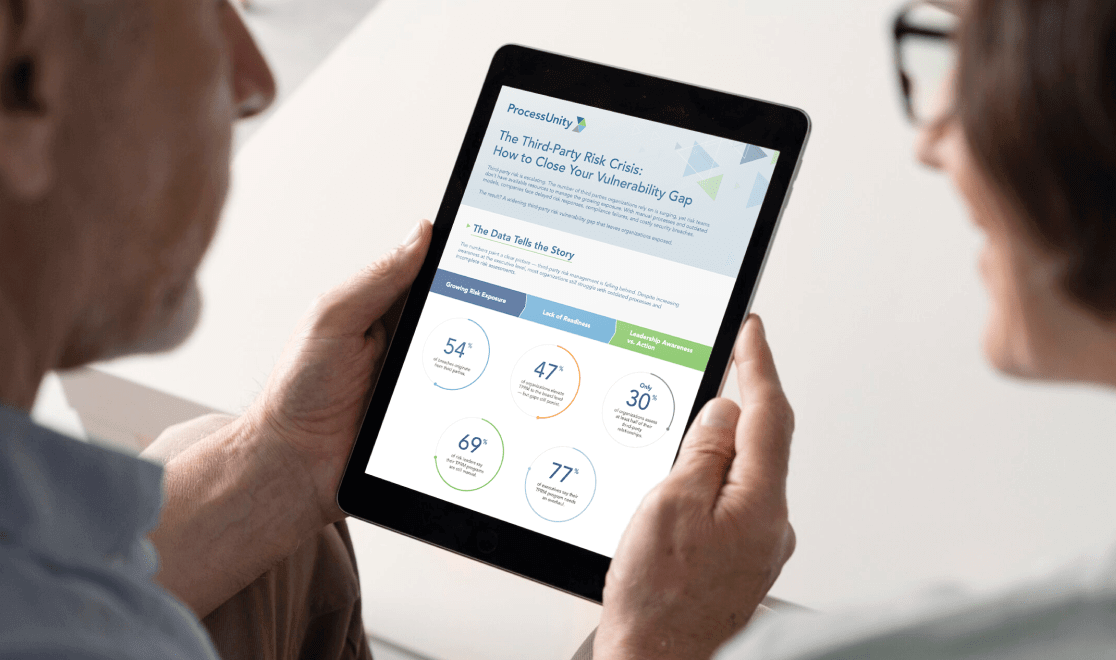
How to Close Your Third-Party Risk...
Is your organization exposed to hidden third-party risks that could create dangerous blind spots in..
Learn More
8 Ways Your Business Benefits from...
Cyber threats are intensifying. Regulatory scrutiny is increasing. Legacy assessments simply can’t keep pace. To..
Learn More
5 Critical Regulations Reshaping TPRM in...
The pressure on financial institutions to manage third-party risk is mounting — and the stakes..
Learn More
10 Critical Third-Party Risk Management Challenges...
Every vendor relationship can introduce potential vulnerabilities to your business, and in today's hyperconnected business..
Learn More
Ensure Ongoing DORA Compliance Across Your...
The Digital Operational Resilience Act (DORA) is a regulatory framework established by the European Union..
Learn More
5 Essential Steps to Modernize Your...
Third-party relationships have become a critical vulnerability point - with 54% of security breaches occurring..
Learn More
Third-party risk: Re-thinking vendor assessments
Third parties can introduce substantial risk into global supply networks, but rigorous vendor risk assessments..
Learn More
ProcessUnity Introduces a Revolutionary Platform to...
Threat and Vulnerability Response Platform Utilizes Proprietary Threat Intelligence to Rapidly Identify Third-party Gaps and..
Learn More
Revolutionizing Response to Emerging Third-Party Cybersecurity...
Introducing ProcessUnity’s New Threat and Vulnerability Response Platform to Quickly Identify Emerging Threats and Assess..
Learn More
How Organizations and Vendors Use a...
A third-party risk exchange is a transformative concept designed to make third-party risk management (TPRM)..
Learn More
ProcessUnity Introduces Industry’s All-In-One Third-Party Risk...
Completes Integration with Global Risk Exchange; Augments Resources to Extend Coverage to More Outsourced Service..
Learn More
Mature Your Cyber Program with a...
Risk-based cybersecurity risk management is the process of identifying, tracking and mitigating the risks to..
Learn More
Controls-Based Versus Risk-Based Cybersecurity Programs
In the face of an escalating regulatory burden and increasingly common data breaches, many teams..
Learn More
Manage Cybersecurity Risk with the SCF...
The Secure Controls Framework (SCF) Risk Management Model can be a powerful tool for teams..
Learn More
Optimize Vendor Onboarding by Aligning with...
During the vendor onboarding process, both cybersecurity and procurement manage the amount of risk brought..
Learn More
3 Takeaways about Anti-Bribery and Corruption...
Anti-bribery and corruption programs grant businesses visibility into their internal practices and third-party networks to..
Learn More
Properly Scoping Vendor Due Diligence Drives...
Properly Scoping Vendor Due Diligence Saves Both Time and Money One of the costliest mistakes..
Learn More
Security Assessments 2.0: The Next Generation...
The more things change, the more they stay the same. It's a well-worn adage that..
Learn More
How to Conduct Third-Party Due Diligence
Identifying and engaging with the right partners is essential to the success of most businesses...
Learn More
Evaluating Security Risk When Onboarding New...
In today’s tightly interwoven supply chains and highly competitive markets, organizations must continuously evaluate and..
Learn More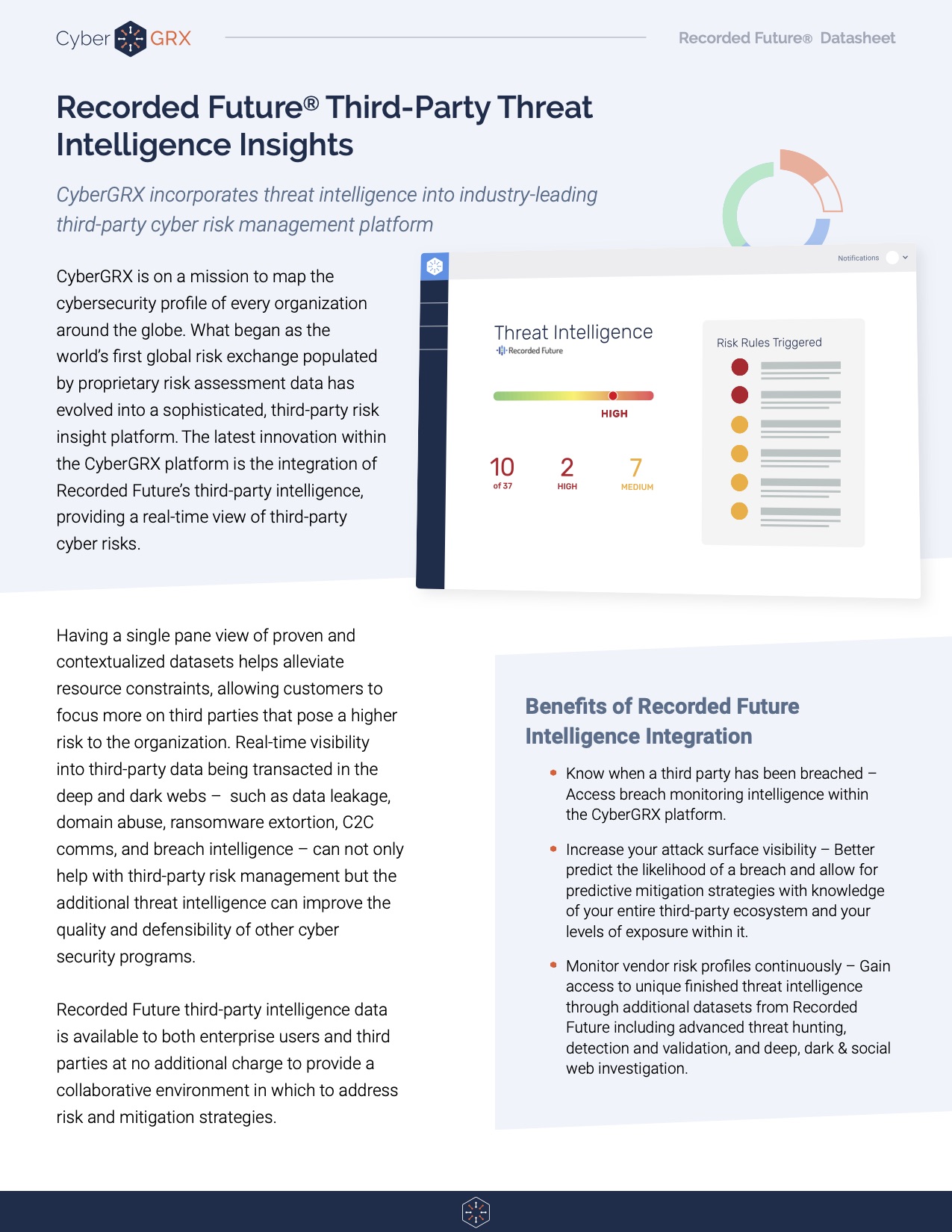
Recorded Future Third-Party Threat Intelligence Insights
Having a single pane view of proven and contextualized datasets helps alleviate resource constraints, allowing..
Learn More
5 Areas to Mitigate Risk in...
If you work within a Vendor Risk Management (VRM) team, you know that third-party risk..
Learn More
5 Tips to Improve Your Vendor...
Vendor due diligence is essential to any third-party risk management program. However, no two due diligence processes are..
Learn More
Inherent Risk vs. Residual Risk in...
Conducting a thorough vendor risk analysis is an integral step in Vendor Risk Management. However,..
Learn More
What is Third-Party Risk Management?
Third-Party Risk Management is the process of identifying, managing and mitigating risks present in a vendor relationship. This..
Learn More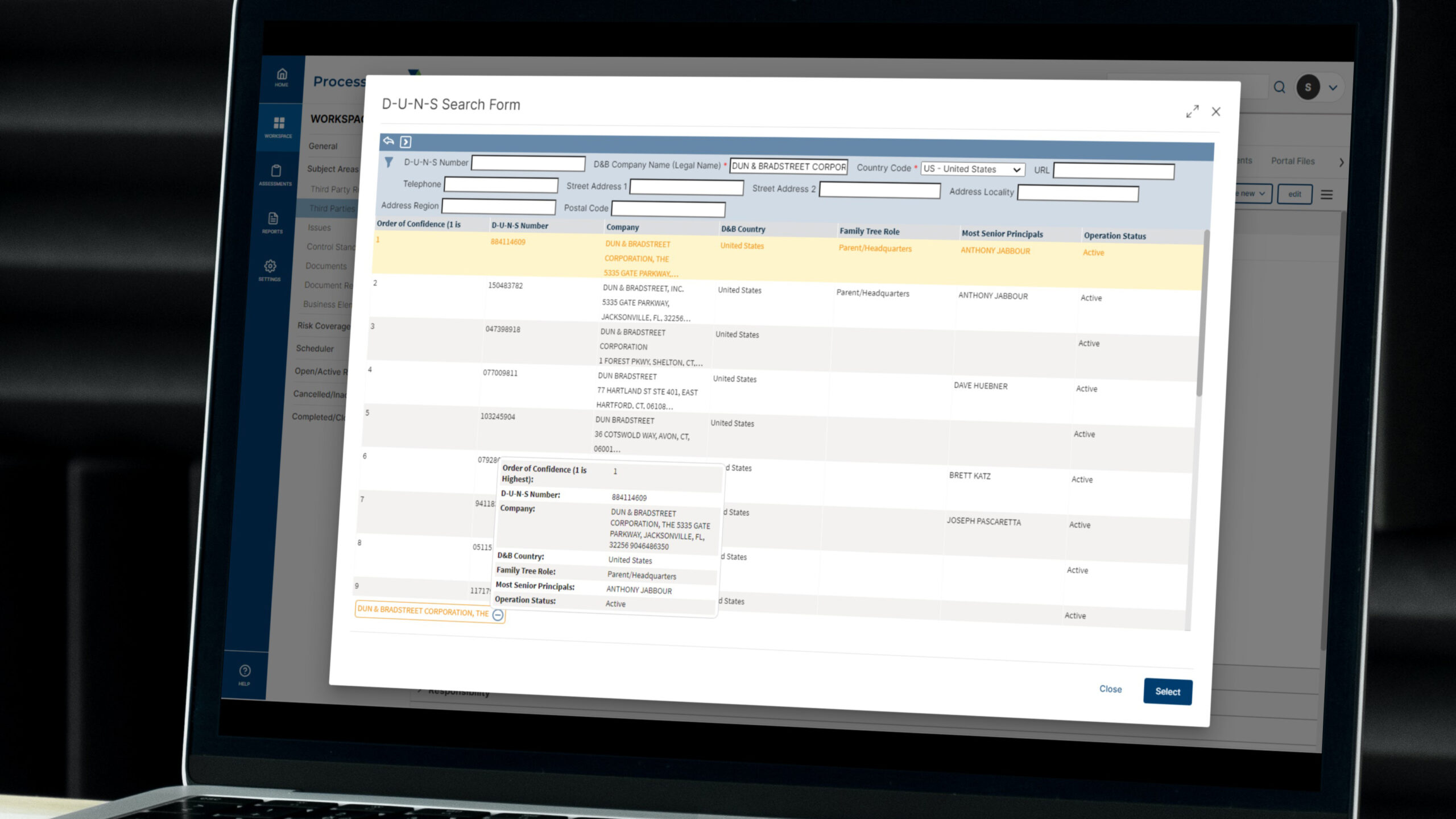
ProcessUnity Vendor Identity Intelligence with Dun...
ProcessUnity Vendor Identity Intelligence seamlessly and automatically incorporates D&B’s D-U-N-S Search and Beneficial Owner Search..
Learn More
Anti-Bribery & Corruption (ABAC) in Business...
The impacts of corruption can be very severe and have been historically well documented. On a political level, corruption – however and wherever..
Learn More
What Is Third-Party Risk Management: The...
The recent SolarWinds breach has reminded news organizations, businesses, and leadership teams around the world..
Learn More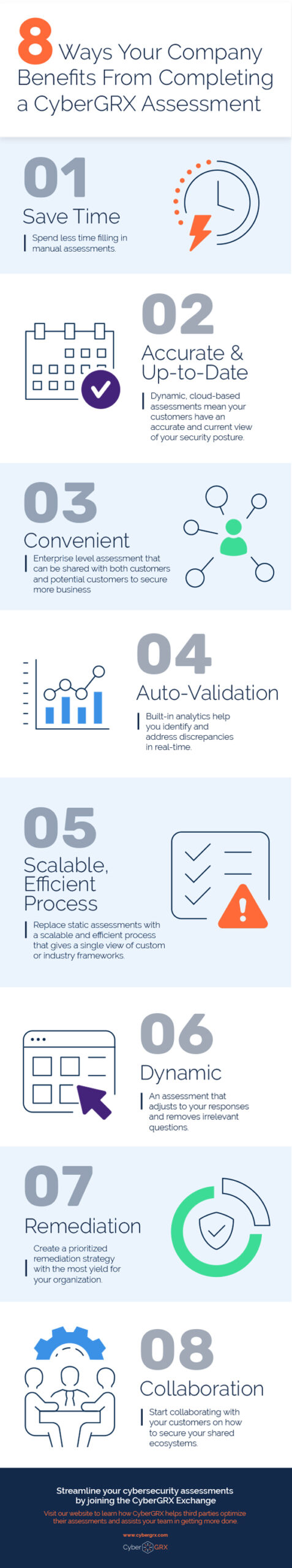
8 Benefits of Completing a CyberGRX...
CyberGRX modernizes and streamlines redundant and inefficient processes that come with shared and static..
Learn More
Third-Party Risk Management Best Practices
New Guide Offers Expert Advice for Effective and Efficient Vendor-Risk Processes A robust, effective, and..
Learn More
Best Practice Program for ProcessUnity Vendor...
ProcessUnity Vendor Risk Management (VRM) protects companies and their brands by reducing risks from third-party vendors and..
Learn More
ProcessUnity Vendor Financial Intelligence Powered By...
ProcessUnity Vendor Financial Intelligence (VFI) with RapidRatings seamlessly incorporates RapidRatings’ financial health ratings into ProcessUnity’s Third-Party..
Learn More
Vendor Screening Intelligence with Refinitiv
ProcessUnity Vendor Screening Intelligence (VSI) embeds LSEG World-Check One’s third-party screening capabilities into ProcessUnity’s Third-Party Risk..
Learn More
How to Stay Ahead of Risk...
Managing risk through pre-contract vendor due diligence in a digitally connected world Thanks to increasing..
Learn MoreAbout Us
ProcessUnity is a leading provider of cloud-based applications for risk and compliance management. The company’s software as a service (SaaS) platform gives organizations the control to assess, measure, and mitigate risk and to ensure the optimal performance of key business processes. ProcessUnity’s flagship solution, ProcessUnity Vendor Risk Management, protects companies and their brands by reducing risks from third-party vendors and suppliers. ProcessUnity helps customers effectively and efficiently assess and monitor both new and existing vendors – from initial due diligence and onboarding through termination. Headquartered outside of Boston, Massachusetts, ProcessUnity is used by the world’s leading financial service firms and commercial enterprises. For more information, visit www.processunity.com.