10 Critical Third-Party Risk Management Challenges and How to Mitigate Them
6 minute read
March 2025
Every vendor relationship can introduce potential vulnerabilities to your business, and in today’s hyperconnected business landscape, it only takes one missed gap to compromise your entire security chain. The numbers tell a sobering story:
- According to the Global Cybersecurity Outlook 2024 report by the World Economic Forum, a staggering 98% of organizations report having at least one third-party partner that has suffered a data breach in the last two years.
- More than 50% of organizations have indirect relationships with over 200 fourth parties that have been breached in the same timeframe, as cited in the same report.
- The IBM Cost of a Data Breach Report 2024 shows that the global average cost of a data breach has hit a record $4.88 million.
For risk management professionals, these statistics underscore the importance of establishing a robust third-party risk management solution for your business.
The Growing Importance of Third-Party Risk Management Solutions
Your organization’s security perimeter now extends far beyond your own walls. Each vendor relationship introduces new risks — cybersecurity vulnerabilities, operational dependencies, compliance challenges, and reputational exposure.
The stakes have never been higher: a single third-party security breach can cascade into devastating consequences for your organization, from regulatory penalties and financial losses, to damaged customer trust. Yet, many organizations still treat vendor risk management as a checkbox exercise, leaving themselves exposed to threats that could cripple their operations.
Forward-thinking companies recognize robust third-party risk management isn’t just about defense — it’s about building resilient business partnerships that drive growth while protecting core assets.
Let’s explore the ten most critical third-party risk management challenges organizations face today and how to address them effectively.
Top 10 Third-Party Risk Management Challenges and How to Mitigate Them Effectively
1. Evolving (and Maturing) Cybersecurity Threats
Supply chain attacks have risen as threat actors increasingly target vendor access credentials and APIs. Since third-party vendors often operate outside your direct security controls, while maintaining privileged system access, they can cause significant exposure to data breaches, malware attacks, and unauthorized system access if not thoroughly assessed.
How to mitigate:
- Implement comprehensive due diligence before onboarding new vendors, verifying their cybersecurity certifications (e.g. ISO 27001 or NIST).
- Deploy continuous monitoring tools to detect and mitigate threats in real time.
- Establish cybersecurity training programs for all third-party vendors.
2. Third-Party Risk Oversight
Most enterprises now manage thousands of third-party relationships, each bringing its own unique risk profile and potential downstream vulnerabilities. Traditional oversight methods fail to capture the individual complexity of modern vendor networks, especially when vendors themselves rely on fourth parties, or operate across multiple jurisdictions. This lack of visibility becomes particularly acute in areas like financial stability, operational resilience, and subcontractor management.
How to mitigate:
- Use a combination of standardized frameworks like NIST or ISO 27001 and customized assessments to properly assess vendors based on their exposure impact to your organization.
- Deploy a centralized third-party risk dashboard for real-time monitoring.
3. Regulatory Compliance
The regulatory landscape has grown increasingly complex with frameworks like DORA, APRA, and ABAC taking shape. Organizations face overlapping compliance obligations across multiple jurisdictions, with each demanding specific data-protection requirements and risk reporting.
How to mitigate:
- Create a compliance checklist for vendors including applicable data protection regulations.
- Conduct regular audits to ensure vendors meet regulatory compliance requirements.
- Collaborate with legal experts to stay updated on new or evolving data protection laws.
4. Vendor Risk Classification
Vendor use cases span various service types and risk levels. Without proper classification, organizations either waste resources over-monitoring low-risk vendors or dangerously under-monitor critical ones.
How to mitigate:
- Use a vendor risk scoring system to classify vendors into tiers based on criticality and risk level.
- Automate vendor classification using AI and pre-completed assessments to reduce errors and inconsistencies.
- Allocate resources strategically, focusing enhanced monitoring and audit efforts on high-risk vendors.
5. Onboarding Cycles
Vendor onboarding processes typically involve multiple departments and can stretch across months, often creating significant business delays. This extended timeline often pressures teams to cut corners in security assessments and due diligence reviews to appease their peers, leading to rushed security assessments and increased exposure to threats.
How to mitigate:
- Standardize pre-contract due diligence templates to eliminate redundancies and clearly state risk assessment needs.
- Automate onboarding workflows to streamline data collection and analysis.
- Use a centralized vendor portal to simplify document submissions, avoid duplicate requests, and streamline communication with third parties.
6. Real-Time Monitoring
Organizations must track both immediate risks, like security breaches, and gradual issues, like deteriorating vendor performance. Traditional point-in-time assessments fail to capture the dynamic nature of vendor risk, while real-time monitoring solutions often generate overwhelming amounts of data without clear prioritization or context.
How to mitigate:
- Implement continuous monitoring tools that provide real-time updates on vendor risks.
- Conduct periodic assessments to ensure ongoing regulatory compliance and alignment with your organization’s security standards.
- Integrate targeted vendor intelligence to streamline due diligence reviews and stay on top of emerging risks.
7. AI and Automation
As vendor networks expand beyond what human teams can effectively manage, manual processes become increasingly unsustainable. Traditional approaches can also introduce consistency problems in risk assessments and monitoring.
How to mitigate:
- Use AI-driven risk management tools to predict and prioritize assessment responses more accurately.
- Embed automation in workflows to accelerate processes and reduce human error.
- Combine AI insights with human expertise to enhance decision-making.
8. Threat Prioritization and Response
Organizations receive a constant stream of alerts about third-party risks, but often lack structured frameworks for distinguishing between critical and routine vulnerabilities. This alert fatigue, combined with siloed response processes across departments, creates dangerous delays in addressing serious threats.
How to mitigate:
- Implement a vendor risk scoring system to prioritize threats based on impact and likelihood.
- Automate threat detection and response processes to eliminate inefficiencies and accelerate mitigation.
- Establish clear escalation protocols to ensure rapid response to high-risk threats.
9. Vendor Assessment Gaps
Standard assessment templates often fail to capture industry-specific risks or unique vendor relationships, creating dangerous blind spots in risk evaluation. These gaps become particularly problematic with vendors who operate in emerging technology sectors or provide novel services that don’t fit traditional risk categories.
How to mitigate:
- Utilize customizable assessment templates to cover key risk areas, while allowing for individual vendor risk data.
- Automate assessment workflows to ensure thorough and timely evaluations.
- Leverage a risk assessment exchange to assess large or complex vendors, and verify vendor assessment data with previously completed responses.
10. Contract Lifecycle Management
Modern vendor contracts contain numerous risk and compliance obligations that require ongoing monitoring and periodic validation. Without systematic management, critical contract provisions — like security requirements, performance metrics, and compliance obligations — become effectively unenforceable.
How to mitigate:
- Standardize risk-based contract templates to streamline pre-contract due diligence and enforce security requirements.
- Centralize contract management to ensure visibility into vendor agreements and performance.
- Automate contract tracking and renewals to prevent lapses and missed compliance updates.
Turn Challenges into Opportunities with an All-in-One TPRM Platform
Every vendor risk challenge highlights an opportunity to strengthen your security posture — if you have the right tools. A comprehensive third-party risk management platform doesn’t just help you manage risks — it transforms your entire approach to vendor relationships.
A comprehensive third-party risk management platform can help you:
- Automate risk assessments and monitoring
- Streamline vendor onboarding
- Ensure continuous TPRM compliance
- Scale your risk management program efficiently
The right third-party risk management solution isn’t just another tool in your security arsenal — it’s a strategic advantage that protects your business while improving operational efficiency.
Take control of your third-party security today.
Explore how a comprehensive third-party risk management solution provider helps you take a proactive approach to protecting your organization.
Ready to transform your third-party risk management program? See how ProcessUnity can help you overcome these 10 common challenges with our comprehensive TPRM Program.
Related Articles

Cut Risk, Not Corners: Streamlining the...
The modern organization relies on a larger, more integrated network of third parties and suppliers..
Learn More
Accelerate Control Reviews with ProcessUnity’s Evidence...
Third-party risk assessments are becoming increasingly complex and resource-intensive. Manual evidence reviews create bottlenecks, inconsistent..
Learn More
5 Cybersecurity Frameworks Financial Institutions Can’t...
Regulatory pressure is intensifying — and financial institutions are feeling the heat. In 2024, the..
Learn More
ProcessUnity Evidence Evaluator: AI-Based Third-Party Controls...
See how ProcessUnity’s GenAI-powered feature simplifies third-party risk assessments. In just 60 seconds, discover how..
Learn More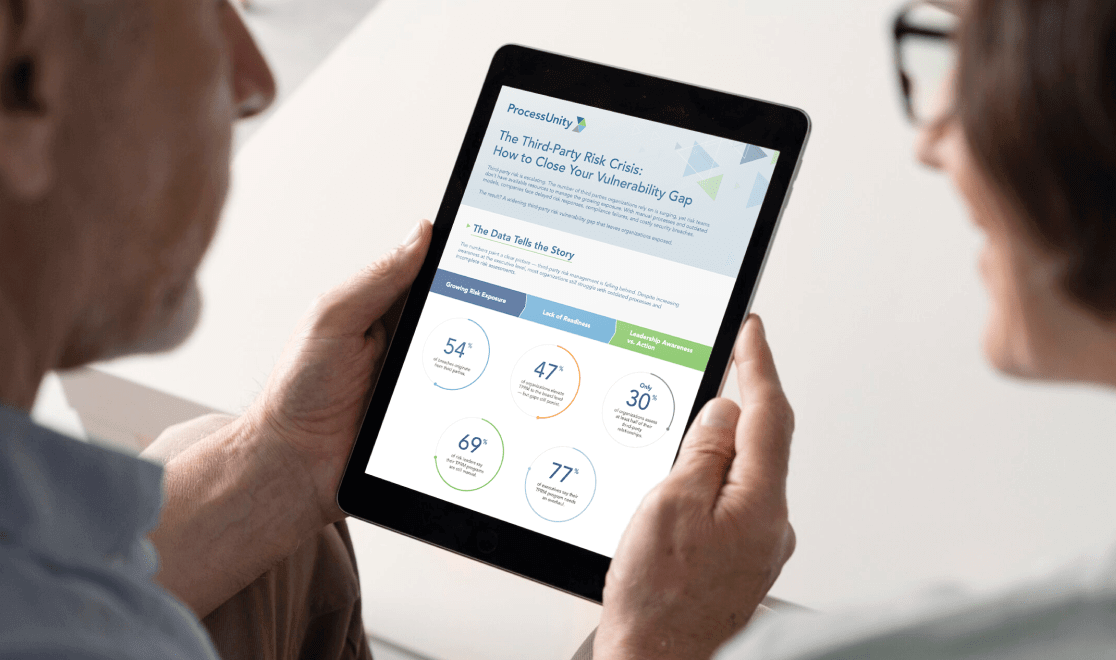
How to Close Your Third-Party Risk...
Is your organization exposed to hidden third-party risks that could create dangerous blind spots in..
Learn More
8 Ways Your Business Benefits from...
Cyber threats are intensifying. Regulatory scrutiny is increasing. Legacy assessments simply can’t keep pace. To..
Learn More
5 Critical Regulations Reshaping TPRM in...
The pressure on financial institutions to manage third-party risk is mounting — and the stakes..
Learn More
How Third-Party Vendor Risk Disrupts Business...
Your third-party vendors are delivering on time, business operations are efficient and planned, and customers..
Learn More
Ensure Ongoing DORA Compliance Across Your...
The Digital Operational Resilience Act (DORA) is a regulatory framework established by the European Union..
Learn More
5 Essential Steps to Modernize Your...
Third-party relationships have become a critical vulnerability point - with 54% of security breaches occurring..
Learn More
Third-party risk: Re-thinking vendor assessments
Third parties can introduce substantial risk into global supply networks, but rigorous vendor risk assessments..
Learn More
ProcessUnity Introduces a Revolutionary Platform to...
Threat and Vulnerability Response Platform Utilizes Proprietary Threat Intelligence to Rapidly Identify Third-party Gaps and..
Learn More
Revolutionizing Response to Emerging Third-Party Cybersecurity...
Introducing ProcessUnity’s New Threat and Vulnerability Response Platform to Quickly Identify Emerging Threats and Assess..
Learn More
How Organizations and Vendors Use a...
A third-party risk exchange is a transformative concept designed to make third-party risk management (TPRM)..
Learn More
ProcessUnity Introduces Industry’s All-In-One Third-Party Risk...
Completes Integration with Global Risk Exchange; Augments Resources to Extend Coverage to More Outsourced Service..
Learn More
Mature Your Cyber Program with a...
Risk-based cybersecurity risk management is the process of identifying, tracking and mitigating the risks to..
Learn More
Controls-Based Versus Risk-Based Cybersecurity Programs
In the face of an escalating regulatory burden and increasingly common data breaches, many teams..
Learn More
Manage Cybersecurity Risk with the SCF...
The Secure Controls Framework (SCF) Risk Management Model can be a powerful tool for teams..
Learn More
Optimize Vendor Onboarding by Aligning with...
During the vendor onboarding process, both cybersecurity and procurement manage the amount of risk brought..
Learn More
3 Takeaways about Anti-Bribery and Corruption...
Anti-bribery and corruption programs grant businesses visibility into their internal practices and third-party networks to..
Learn More
Properly Scoping Vendor Due Diligence Drives...
Properly Scoping Vendor Due Diligence Saves Both Time and Money One of the costliest mistakes..
Learn More
Security Assessments 2.0: The Next Generation...
The more things change, the more they stay the same. It's a well-worn adage that..
Learn More
How to Conduct Third-Party Due Diligence
Identifying and engaging with the right partners is essential to the success of most businesses...
Learn More
Evaluating Security Risk When Onboarding New...
In today’s tightly interwoven supply chains and highly competitive markets, organizations must continuously evaluate and..
Learn More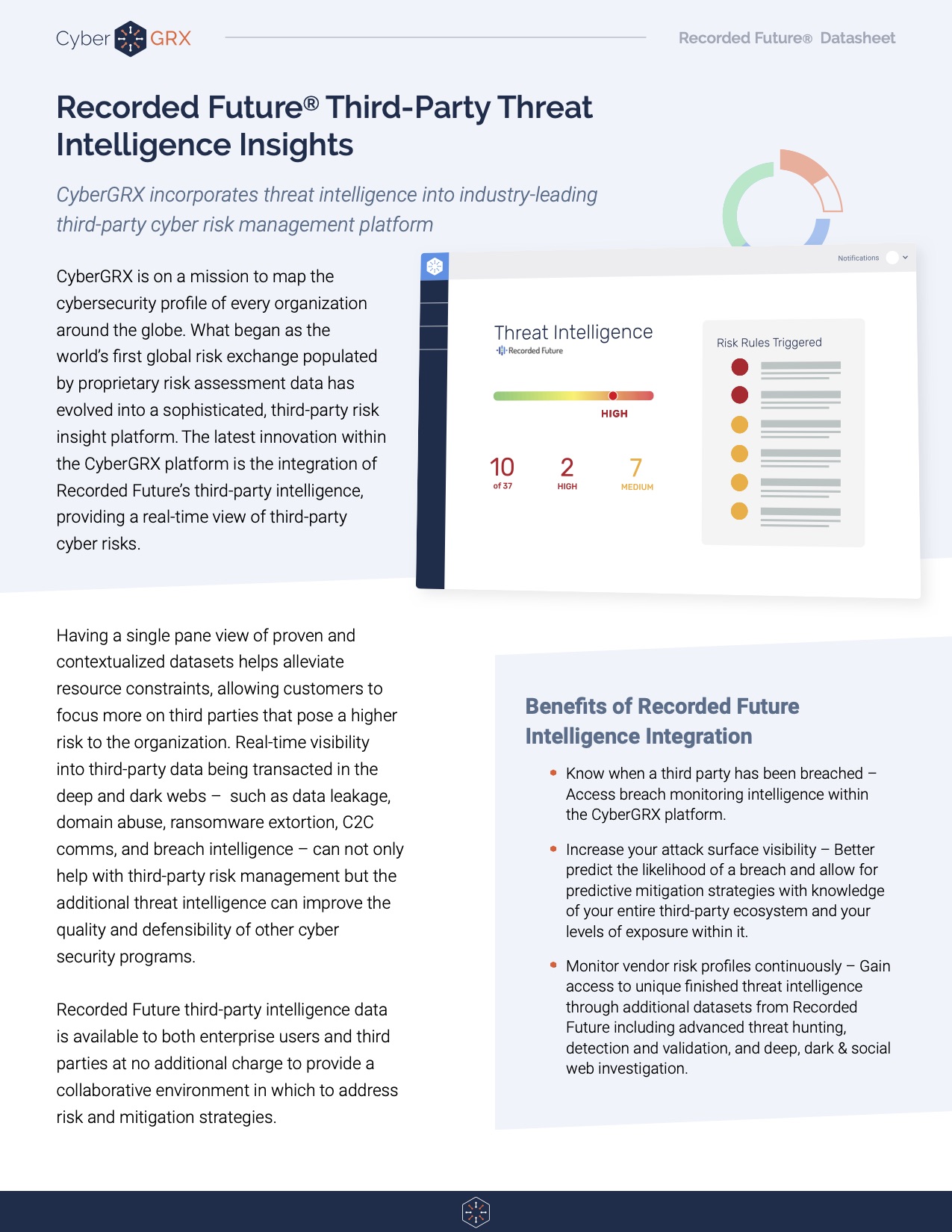
Recorded Future Third-Party Threat Intelligence Insights
Having a single pane view of proven and contextualized datasets helps alleviate resource constraints, allowing..
Learn More
5 Areas to Mitigate Risk in...
If you work within a Vendor Risk Management (VRM) team, you know that third-party risk..
Learn More
5 Tips to Improve Your Vendor...
Vendor due diligence is essential to any third-party risk management program. However, no two due diligence processes are..
Learn More
Inherent Risk vs. Residual Risk in...
Conducting a thorough vendor risk analysis is an integral step in Vendor Risk Management. However,..
Learn More
What is Third-Party Risk Management?
Third-Party Risk Management is the process of identifying, managing and mitigating risks present in a vendor relationship. This..
Learn More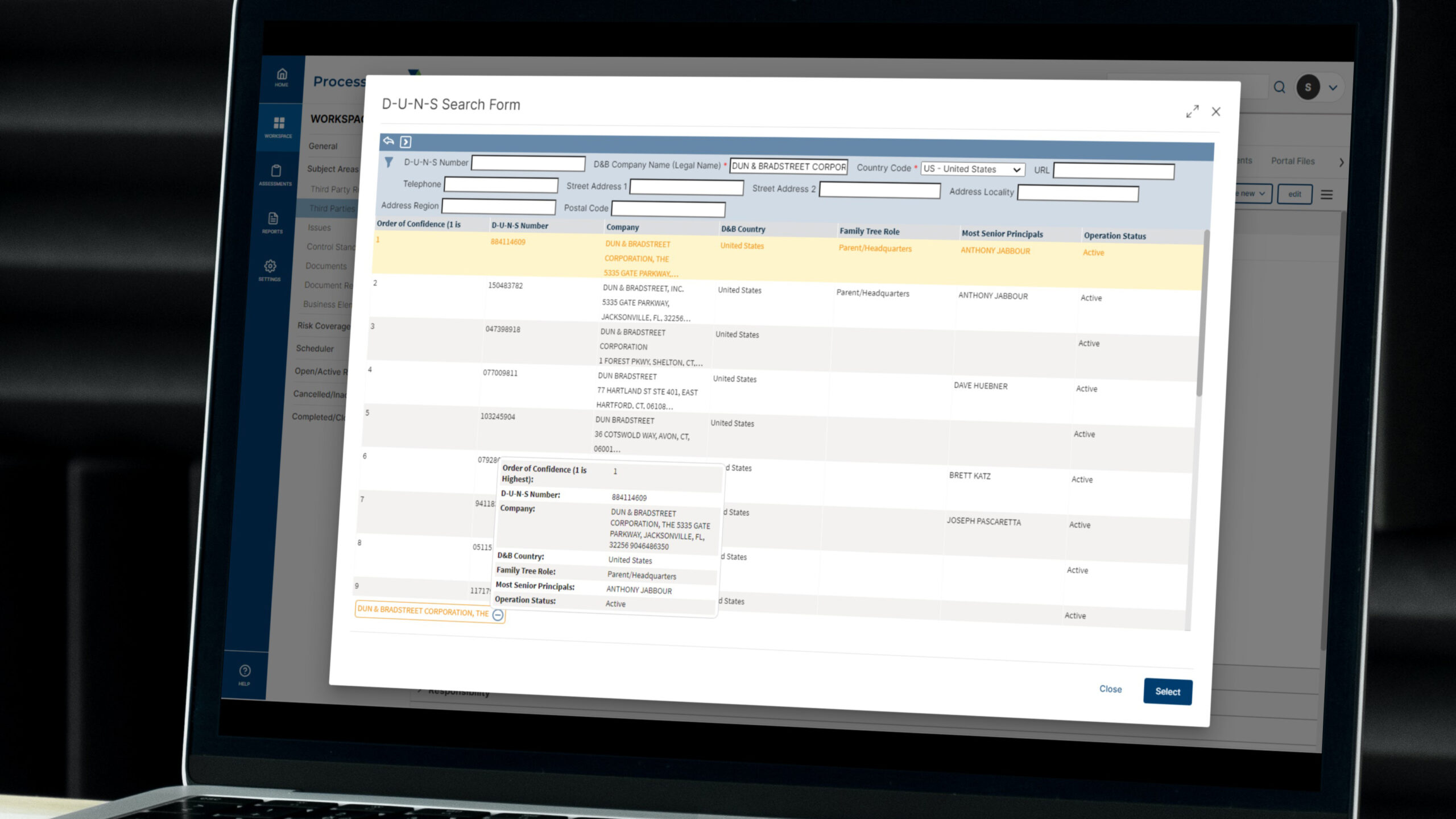
ProcessUnity Vendor Identity Intelligence with Dun...
ProcessUnity Vendor Identity Intelligence seamlessly and automatically incorporates D&B’s D-U-N-S Search and Beneficial Owner Search..
Learn More
Anti-Bribery & Corruption (ABAC) in Business...
The impacts of corruption can be very severe and have been historically well documented. On a political level, corruption – however and wherever..
Learn More
What Is Third-Party Risk Management: The...
The recent SolarWinds breach has reminded news organizations, businesses, and leadership teams around the world..
Learn More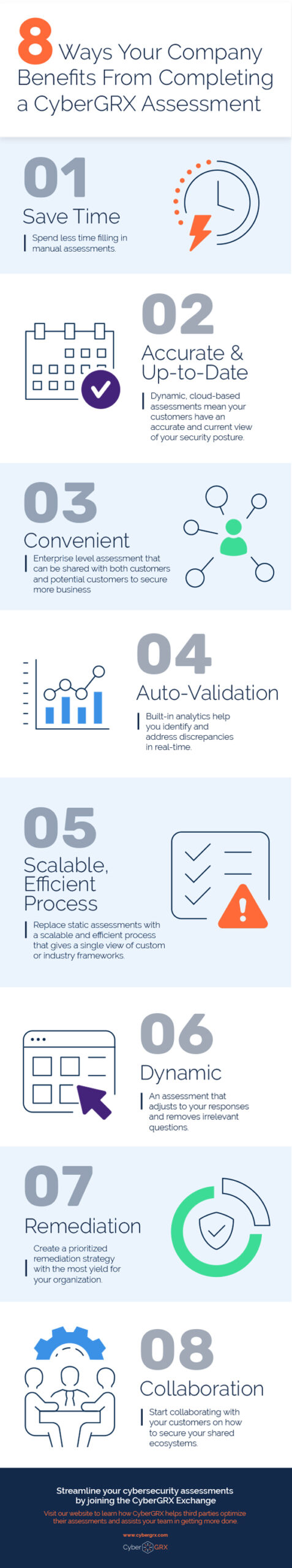
8 Benefits of Completing a CyberGRX...
CyberGRX modernizes and streamlines redundant and inefficient processes that come with shared and static..
Learn More
Third-Party Risk Management Best Practices
New Guide Offers Expert Advice for Effective and Efficient Vendor-Risk Processes A robust, effective, and..
Learn More
Best Practice Program for ProcessUnity Vendor...
ProcessUnity Vendor Risk Management (VRM) protects companies and their brands by reducing risks from third-party vendors and..
Learn More
ProcessUnity Vendor Financial Intelligence Powered By...
ProcessUnity Vendor Financial Intelligence (VFI) with RapidRatings seamlessly incorporates RapidRatings’ financial health ratings into ProcessUnity’s Third-Party..
Learn More
Vendor Screening Intelligence with Refinitiv
ProcessUnity Vendor Screening Intelligence (VSI) embeds LSEG World-Check One’s third-party screening capabilities into ProcessUnity’s Third-Party Risk..
Learn More
How to Stay Ahead of Risk...
Managing risk through pre-contract vendor due diligence in a digitally connected world Thanks to increasing..
Learn MoreAbout Us
ProcessUnity is a leading provider of cloud-based applications for risk and compliance management. The company’s software as a service (SaaS) platform gives organizations the control to assess, measure, and mitigate risk and to ensure the optimal performance of key business processes. ProcessUnity’s flagship solution, ProcessUnity Vendor Risk Management, protects companies and their brands by reducing risks from third-party vendors and suppliers. ProcessUnity helps customers effectively and efficiently assess and monitor both new and existing vendors – from initial due diligence and onboarding through termination. Headquartered outside of Boston, Massachusetts, ProcessUnity is used by the world’s leading financial service firms and commercial enterprises. For more information, visit www.processunity.com.