Featured Resources
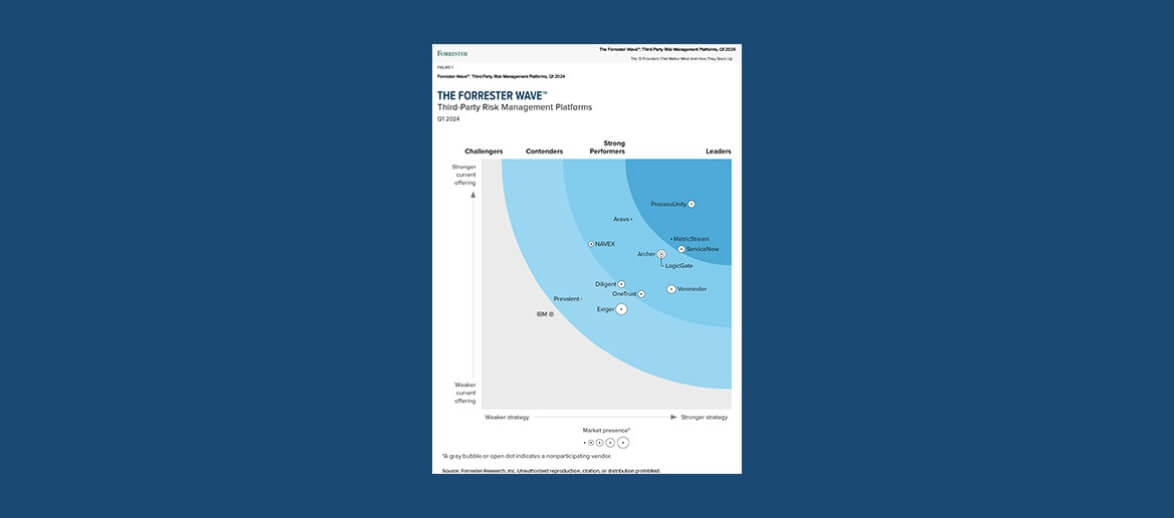
ProcessUnity is a Leader in The Forrester Wave™: Third-Party Risk Management Platforms
Content Library
The State of Procurement: Overcoming Strategic Challenges & Driving Innovation
Procurement teams are embracing new technologies and artificial intelligence, but they still have a long way to go before reaching full maturity. Leaders feel satisfied with their core technology tools despite significant challenges, including limited budgets and a lack of strategic alignment within their organizations. The state of procurement over the next 12 months will […]
The TPRM Evolution Roadmap: Moving from Questionnaire-Based to Data-Driven
Questionnaire-first assessments were built for a simpler risk landscape. In today’s risk landscape, they slow onboarding, limit visibility, and force organizations to react to third-party risk instead of proactively managing it. This guide outlines a clear evolution from manual, questionnaire-driven assessments to data-first, AI-powered TPRM. See how ProcessUnity helps organizations modernize in structured phases, unlocking […]
The Future of TPRM: 5 Innovations Redefining TPRM in 2026
Third-party risk management is at a turning point. For years, risk teams have wrestled with manual evidence reviews, endless back-and-forth questionnaires, and siloed data sources that provide only partial visibility into third-party risk. The pace of innovation is accelerating, and the next wave of TPRM tools promises to reshape how organizations assess, monitor, and manage […]
The TPRM Advantage: How ProcessUnity Stacks Up Against Other Platforms
As third-party risk grows more complex, selecting the right TPRM platform is critical. Many solutions claim end-to-end coverage, but few deliver the automation, easy integration, and data required to manage today’s risks effectively.
Third-Party Risk Management Implementation Roadmap: 6-Step Guide for Enterprises
In today’s hyperconnected environment, where 98% of organizations have at least one third-party partner that has suffered a breach in the past two years, a mature third-party risk management (TPRM) program is no longer optional. It’s essential. The Importance of Structured Third-Party Risk Management Implementation Implementing a TPRM program that is both comprehensive and scalable, […]
A Modern Four-Step Playbook for Managing Emerging Vulnerabilities Across Your Third-Party Ecosystem
When a new vulnerability appears in the wild, security and third-party risk teams feel the pressure immediately. A single CVE can turn into a global incident in a matter of hours, and executives want fast, confident answers about whether their organization is exposed. Modern-day vendor ecosystems are vast and interconnected though, and most teams don’t […]