Cybersecurity Risk Management
ProcessUnity and The Secure Controls Framework (SCF)
Automate control mapping, control evaluation and evidence collection with ProcessUnity for Cybersecurity Risk Management to seamlessly align your cybersecurity program with the Secure Controls Framework (SCF).
Leverage ProcessUnity to align your cybersecurity program with a best practice methodology from the Secure Controls Framework (SCF). Our integration reduces the effort of manual mapping and simplifies your control activities with the SCF’s control mappings to over 175 frameworks, regulations and standards prepared out of the box, such as ISO 27001, NIST and PCI DSS. Our platform improves your cyber readiness with pre-built workflows for assessing risks and controls using SCF methodology.
Key Benefits
- Align with a predefined best practice methodology
- Test one control, satisfy multiple program requirements
- Keep controls up to date with regulation, standard and/or framework changes
- Prioritize cyber risk mitigation
- Demonstrate cyber readiness
ProcessUnity + The Secure Controls Framework
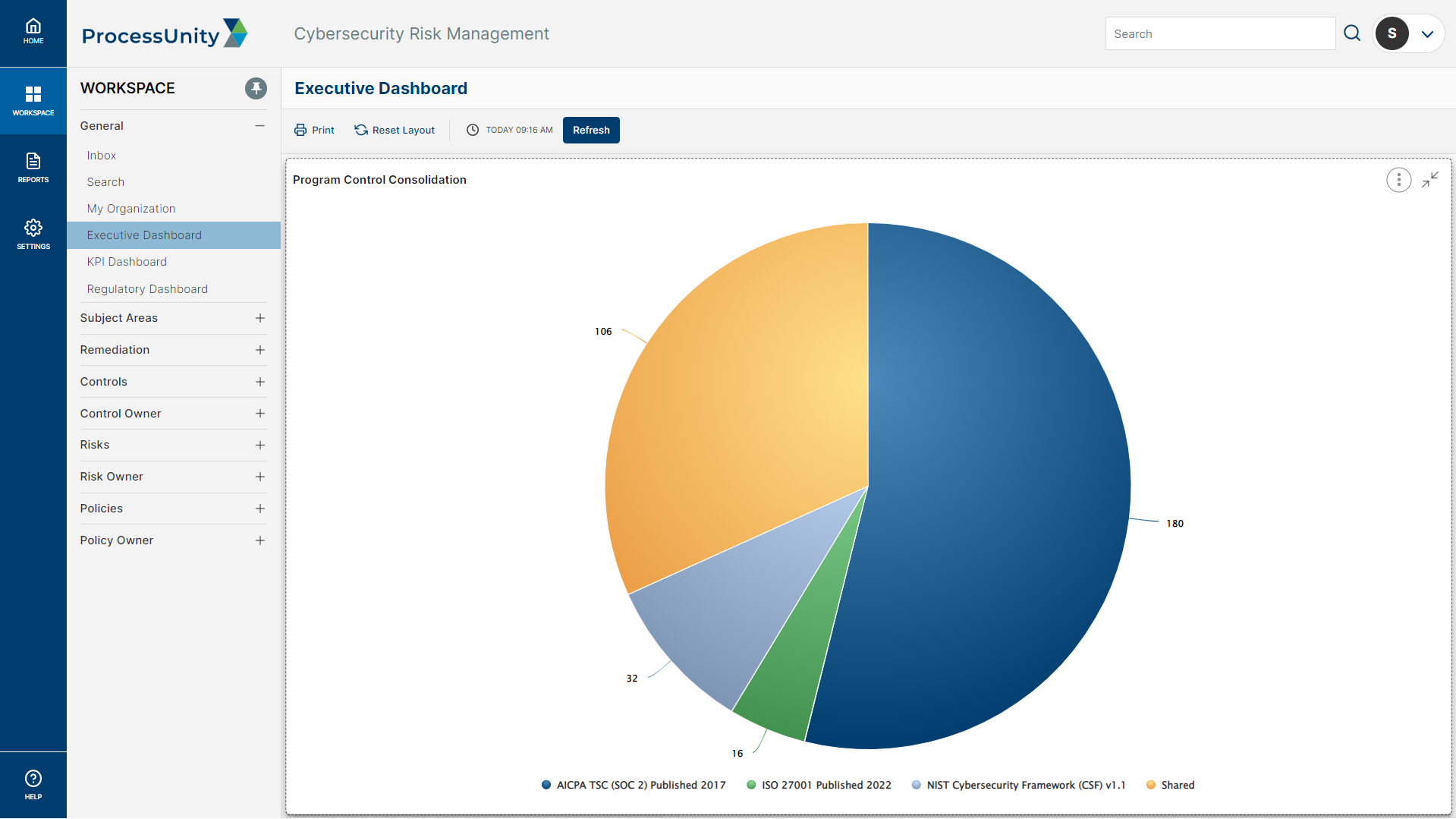
The SCF is a “Rosetta Stone” approach to cybersecurity controls, mapping controls across best practice frameworks and statutory, regulatory and contractual obligations. Our platform guides you through control library creation leveraging SCF common controls. In just a few clicks, you select your relevant requirements, then the platform generates a ready-to-use control set mapped to your requirements. The control set can be easily aligned with organizational units, business owners, risks and policies and procedures.
ProcessUnity seamlessly updates your mapped controls when framework or regulatory updates are made, eliminating the fragmentation and potential risk exposure that often occurs with changes.
ProcessUnity + the SCF Security & Privacy Capability Model (SP-CMM)
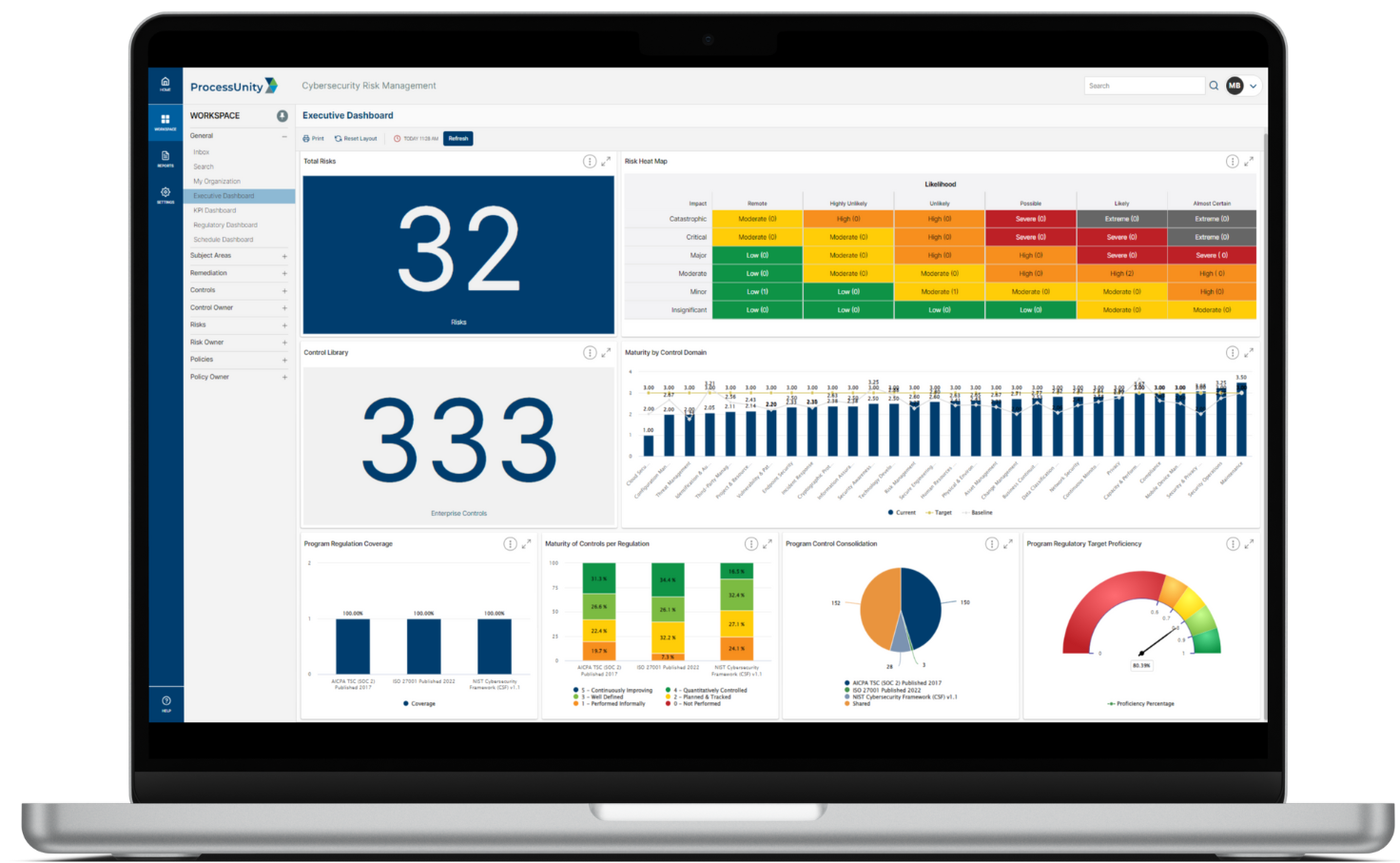
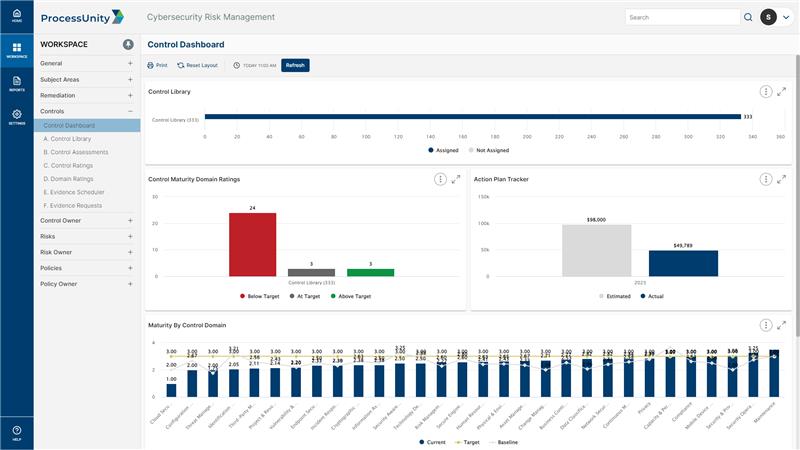
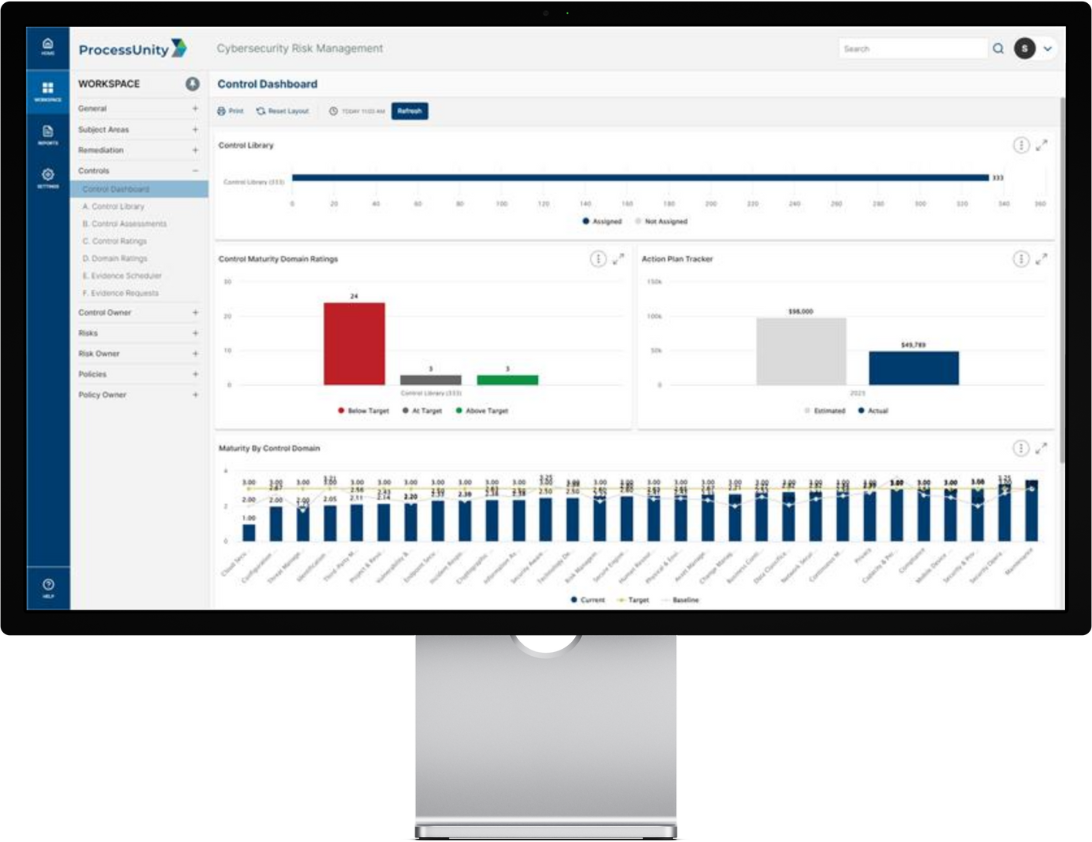
ProcessUnity reduces objectivity in establishing and evaluating cybersecurity controls by aligning your program with the SCF SP-CMM. Our platform provides pre-built workflows for distributing control assessments on your schedule, then automatically assigns ownership to provide an evaluation against a controls maturity and effectiveness. Leveraging the SP-CMM criteria, you assign maturity ratings to your controls, with the ability to create action plans directly from the assessment result. The platform tracks your maturity and effectiveness ratings against your risks and regulatory requirements, providing visibility into domain and program level gaps.
ProcessUnity + the SCF Security & Privacy Risk Management Model (SP-RMM)
ProcessUnity establishes a proven model to identify, assess, report and mitigate cyber risks by leveraging the SCF SP-RMM. Our pre-built risk assessment workflows allow you to input key risk factors such as likelihood and impact, then ProcessUnity automatically calculates inherent and residual risk. You can immediately enforce accountability for open issues by developing action plans to reduce, avoid, transfer or accept the risk directly from the assessment result. Once you assign risk ratings, risks are tracked within a central cybersecurity risk register. Our platform provides complete visibility via real-time reporting on risk posture, trends and mitigating controls.
About ProcessUnity for Cybersecurity Risk Management
ProcessUnity for Cybersecurity Risk Management enables the CISO to prove cyber readiness with a single platform to monitor cyber risks, improve mitigating controls and prioritize program activities. Powered by automation, the platform is purpose-built to create a defensible cybersecurity risk management platform that bolsters the organization’s resilience.
Request a Demo: ProcessUnity's Cybersecurity Risk Management Platform
Hundreds of organizations worldwide rely on ProcessUnity Cybersecurity Risk Management to implement a centralized system of record for managing cybersecurity activities across the organization. Contact us to start your journey today!
Request a Demo: ProcessUnity's Cybersecurity Risk Management Platform