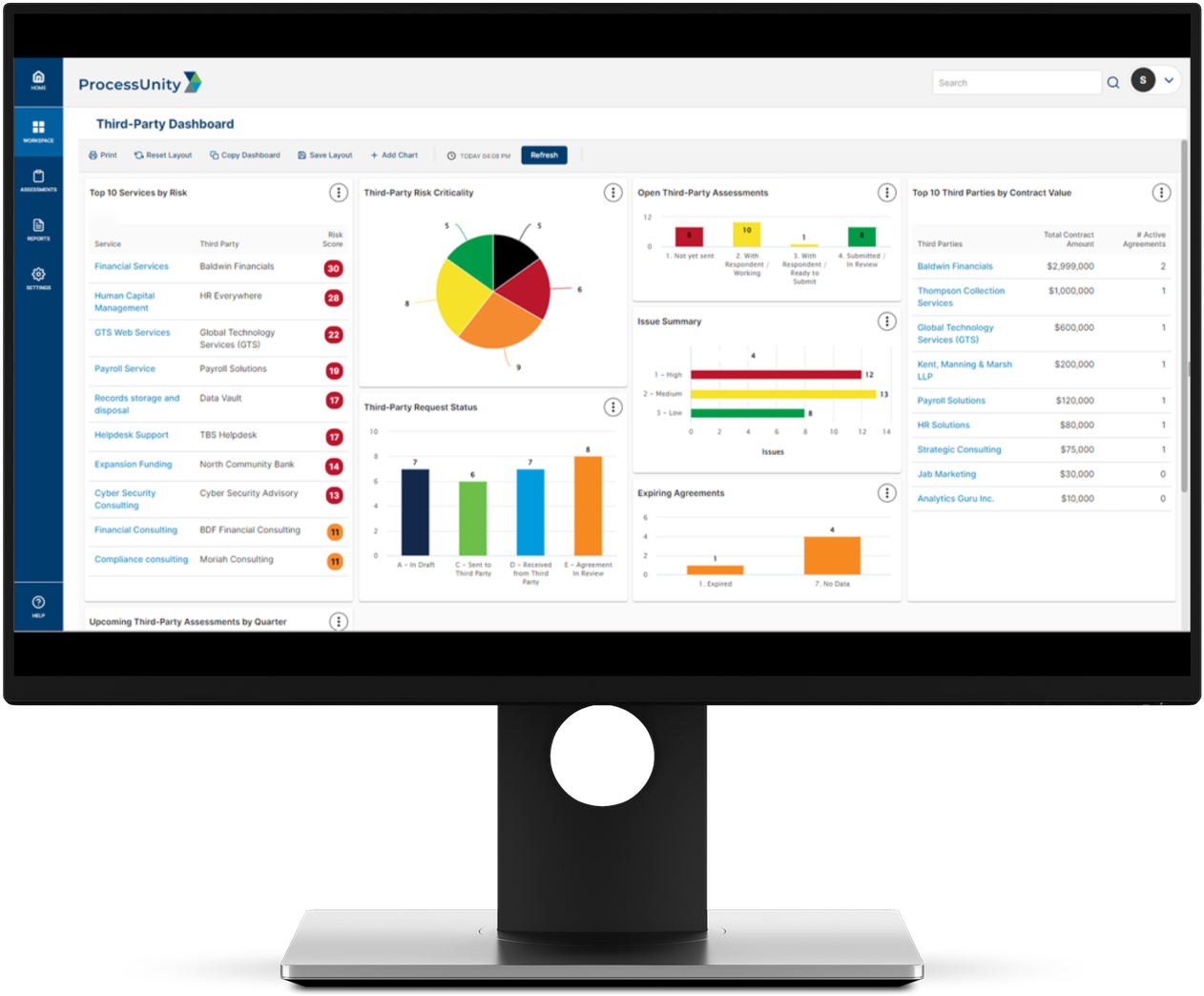
ProcessUnity’s Third-Party Risk Management Maturity Model
Your goals ultimately determine the extent of your Third-Party Risk Management investment. No matter where you are, there is always an opportunity for growth: your program is one that will mature over time, increasing in value as you gain experience. But the key thing is to start with an honest assessment of where you are and where you’d like to go. Use the following Maturity Matrix as a check-up, or as a foundation for further inquiry among your colleagues, to help you determine where you are and where you’d like to go.
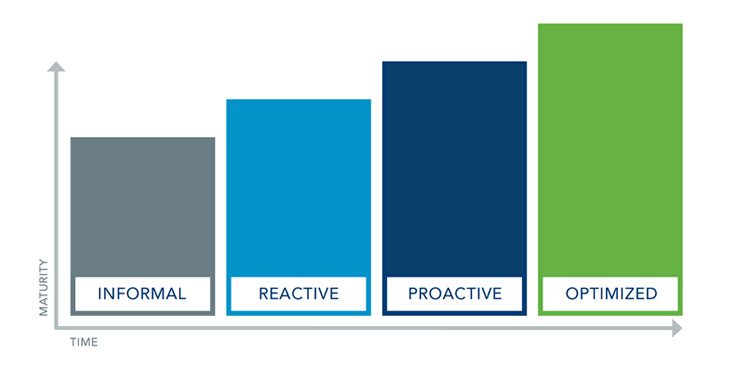
THE ORGANIZATION |
|||
INFORMAL |
REACTIVE |
PROACTIVE |
OPTIMIZED |
|---|---|---|---|
|
|
|
|
POLICY AND PROCEDURES |
|||
INFORMAL |
REACTIVE |
PROACTIVE |
OPTIMIZED |
|---|---|---|---|
|
|
|
|
PROCESSES |
|||
INFORMAL |
REACTIVE |
PROACTIVE |
OPTIMIZED |
|---|---|---|---|
|
|
|
|
RISK ASSESSMENT METHODOLOGY |
|||
INFORMAL |
REACTIVE |
PROACTIVE |
OPTIMIZED |
|---|---|---|---|
|
|
|
|
THIRD PARTIES |
|||
INFORMAL |
REACTIVE |
PROACTIVE |
OPTIMIZED |
|---|---|---|---|
|
|
|
|
SUPPORTING TECHNOLOGIES |
|||
INFORMAL |
REACTIVE |
PROACTIVE |
OPTIMIZED |
|---|---|---|---|
|
|
|
|
REGULATORY PREPAREDNESS / STATURE |
|||
INFORMAL |
REACTIVE |
PROACTIVE |
OPTIMIZED |
|---|---|---|---|
|
|
|
|
STANDARDS ALIGNMENT |
|||
INFORMAL |
REACTIVE |
PROACTIVE |
OPTIMIZED |
|---|---|---|---|
|
|
|
|
Ready to begin your journey to a more mature Third-Party Risk Management program? Contact us today.
Request a Demo: ProcessUnity's Risk Management Platform
Schedule your personalized demo of our award-winning software and start your journey to a more mature, automated program.
Request a Demo: ProcessUnity's Risk Management Platform