ProcessUnity Digital Operational Resilience Act (DORA)
Digital Operational Resilience Act (DORA) Compliance
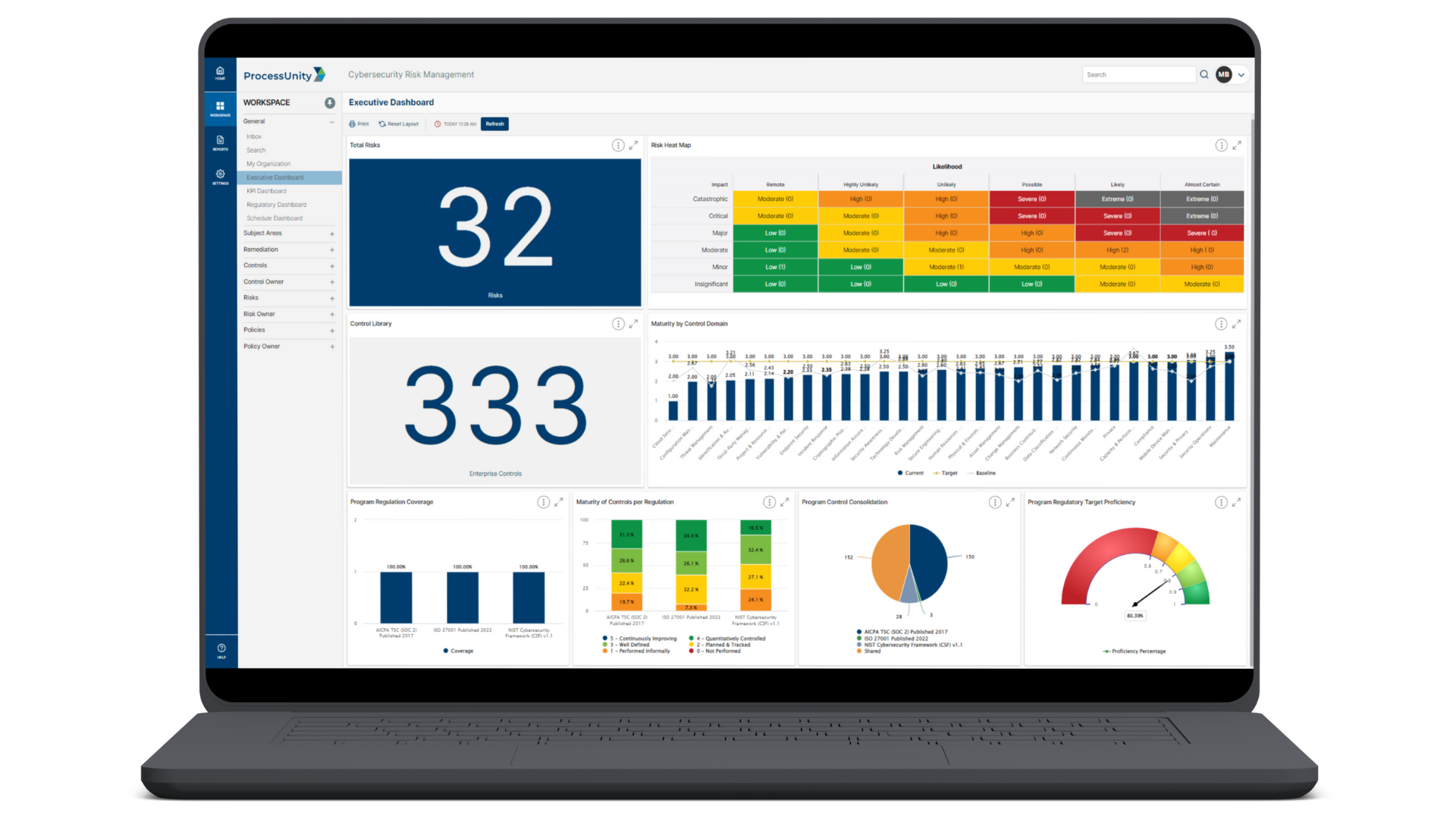
The Digital Operational Resilience Act (DORA) is not just a regulatory mandate—it’s a crucial framework for safeguarding your organization against third-party risk. Mature your third-party risk management (TPRM) program and ensure compliance with DORA without disrupting your day-to-day operations with ProcessUnity.
Key Features and Benefits:
Standardized DORA Third-Party Risk Management
-
Streamlined Onboarding:
Quickly validate the alignment of new third parties with DORA standards using pre-built onboarding steps, ensuring a complete risk profile.
-
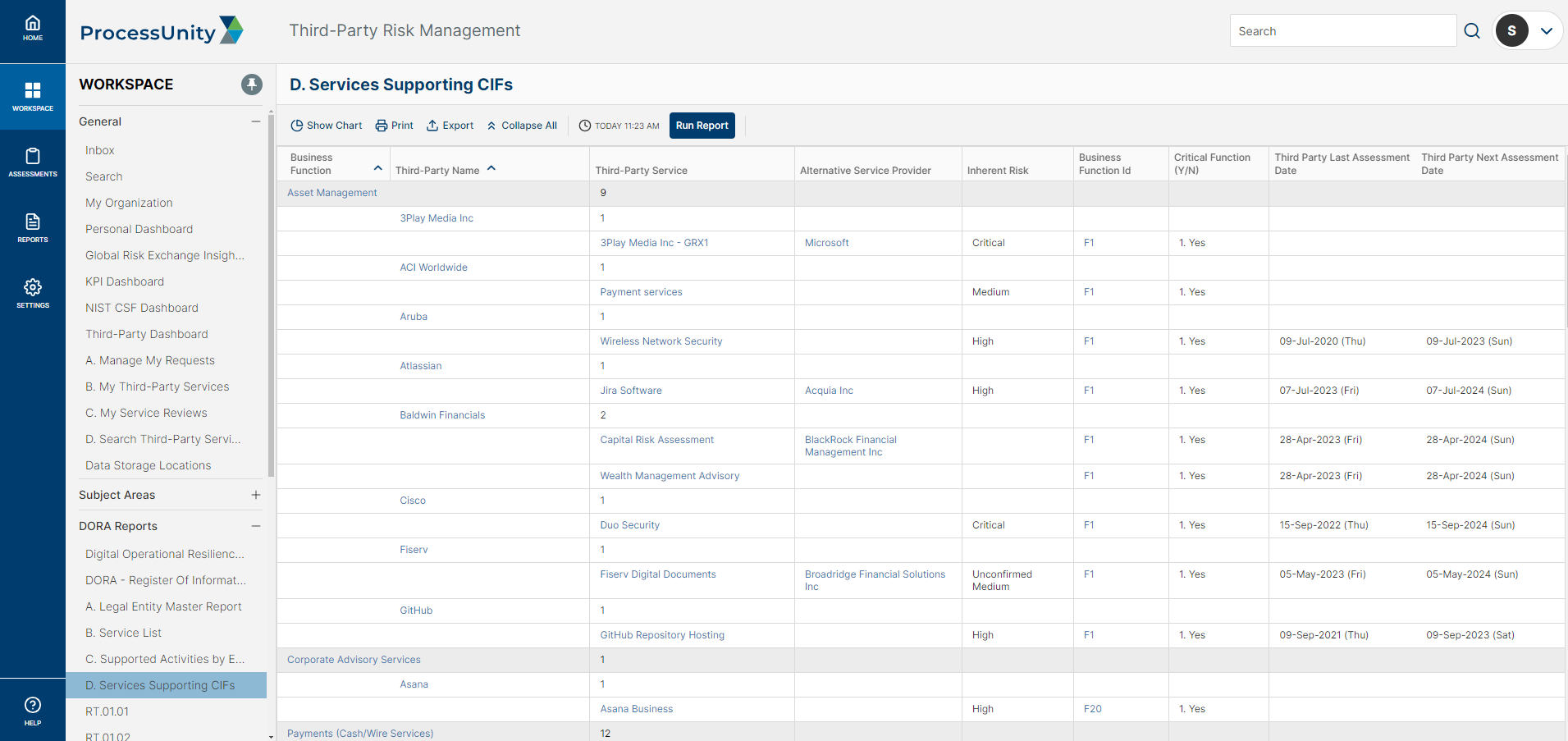
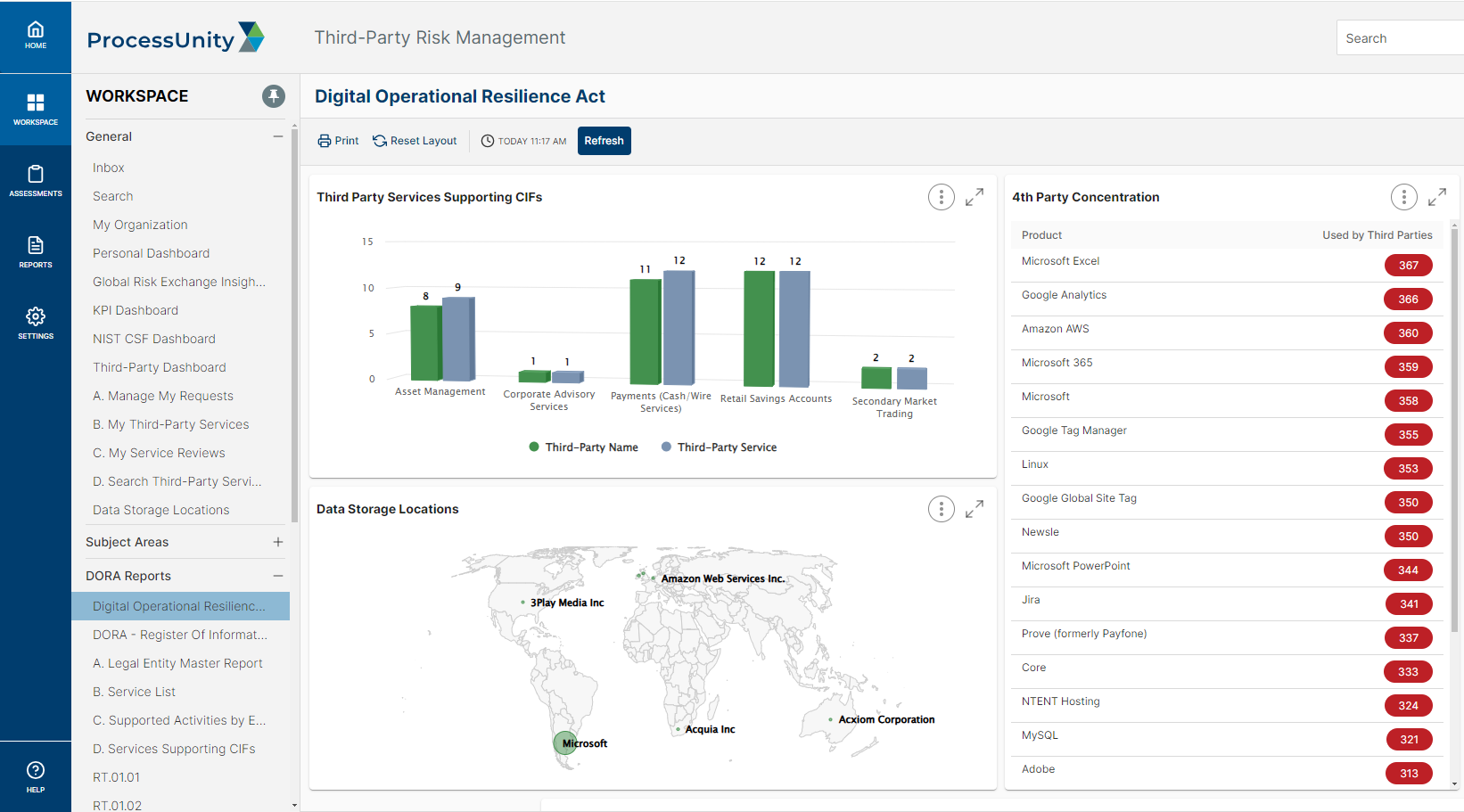
Critical Third-Party Identification:
Leverage a configurable questionnaire to identify and risk-rank your most critical third-party service providers, with streamlined identification of ICT services supporting critical functions.
-
Automated Third-Party Assessments:
Capture essential information required by DORA through automated workflows, including organizational data, intra-company relationships, contractual language, and critical business functions.
-
Continuous Monitoring:
Automate annual due diligence reviews and supplement assessment data with insights into weak third-party controls, ensuring ongoing compliance with DORA.
Incident Response and Reporting
-
Rapid Incident Response:
Develop a mechanism for swift incident response using incident management workflows. Track third-party incidents through to remediation, ensuring compliance with DORA’s strict incident reporting timelines.
-
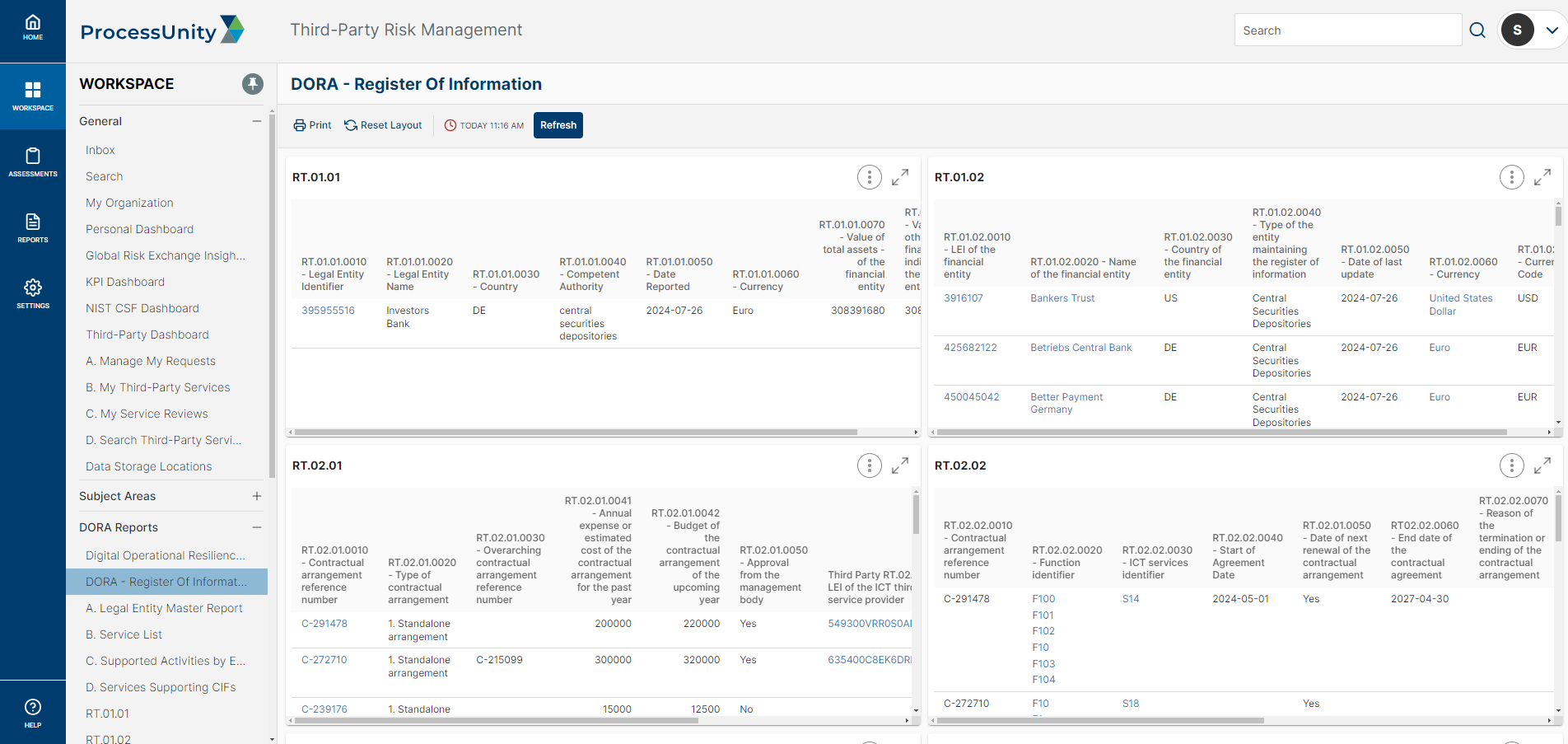
Register of Information:
Simplify the process of collecting, preparing, and presenting data in the Register of Information by automatically populating it from key sources and exporting it with a click.
ProcessUnity’s DORA Components
- Centralized ICT Risk Framework
- Register of Information
- Third-Party Control Assessments
- Standardized TPRM Workflow
- CIF Third Party Identification and Substitutability Planning
- Subcontractor / Nth Party Risk Evaluation
- Continuous Third-Party Control Gap Identification
- Rapid Incident Response and Reporting
- Automated Data Preparation and Export for the Register of Information
Why Choose ProcessUnity for DORA Compliance?
- Efficiency: Reduce the time and effort needed to prepare for DORA compliance.
- Resilience: Maintain resilient operations in the event of a third-party failure and make operational resilience a competitive advantage.
- Trust: Strengthen trust with customers and business partners through robust third-party risk management.
Ready to Learn More? Contact us to discuss your requirements and learn how ProcessUnity DORA enables you to achieve compliance and strengthen your third-party risk management program
Request a Demo: ProcessUnity's DORA Third Party Risk Management Solution
ProcessUnity for DORA streamlines your adherence to new ICT security mandates. Schedule a call today to learn how ProcessUnity for DORA can help you implement cybersecurity risk management best practices internally and throughout your supply chain.
Request a Demo: ProcessUnity's DORA Third Party Risk Management Solution