Enable Cybersecurity Accountability
Throughout the Enterprise
Whether you’re a CISO that needs to support compliance efforts, or an internal assessor tasked with evaluating controls, maximizing the effectiveness of a cybersecurity program can be challenging. Often there are many moving parts within a cybersecurity program – regulations, high-value assets, third parties, threats and their respective downstream owners – making it difficult to achieve a genuine sense of your cybersecurity risk. How can you ensure that your controls adequately meet security objectives to protect your high-value assets and prove compliance?
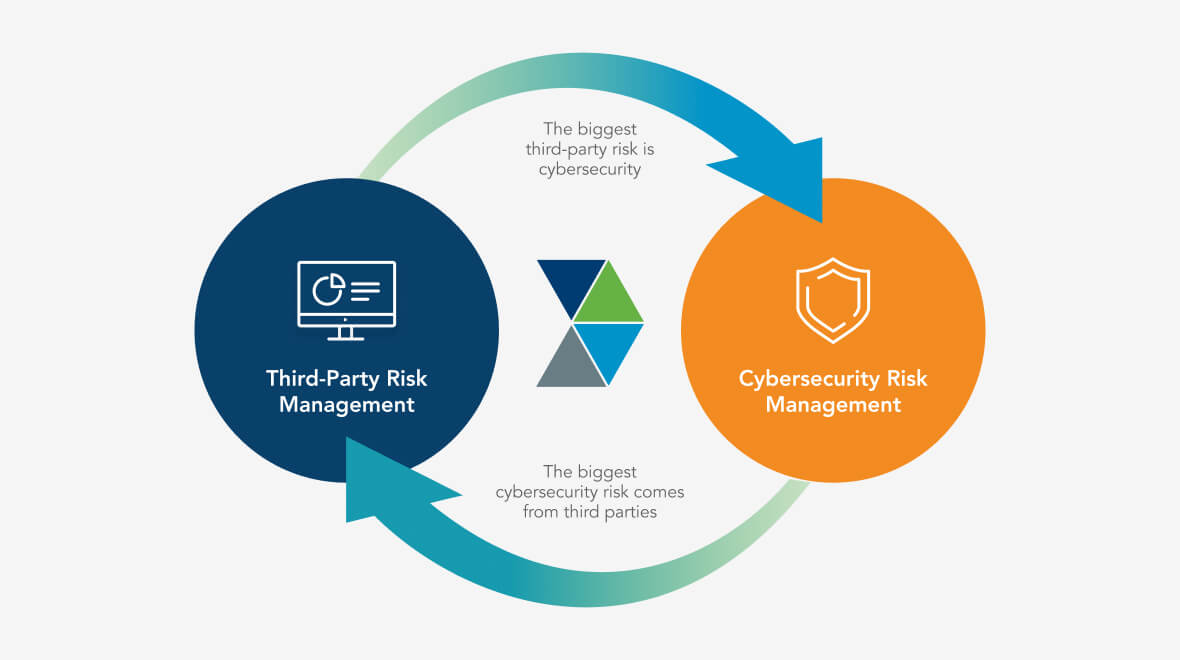
Cybersecurity Risk Management Highlights
Provides complete visibility into your cyber risks in an industry-standard heatmap organized by criticality, allowing you to proactively monitor risks, lower their severity through targeted action plans, and deliver risk summaries to the right stakeholders.
Combines your program data and control framework(s) into a consolidated, cross-mapped framework that leverages the overlap between controls and internal policies to eliminate redundancy.
Ensures alignment with the frameworks, regulations, and standards relevant to your organization’s compliance and certification efforts.
Reveals control and domain-level gaps across your control library, pinpointing the updates needed to bolster your organization’s resilience.




Why ProcessUnity Cybersecurity Risk Management?
Optimizing Cyber Risk Visibility and Control
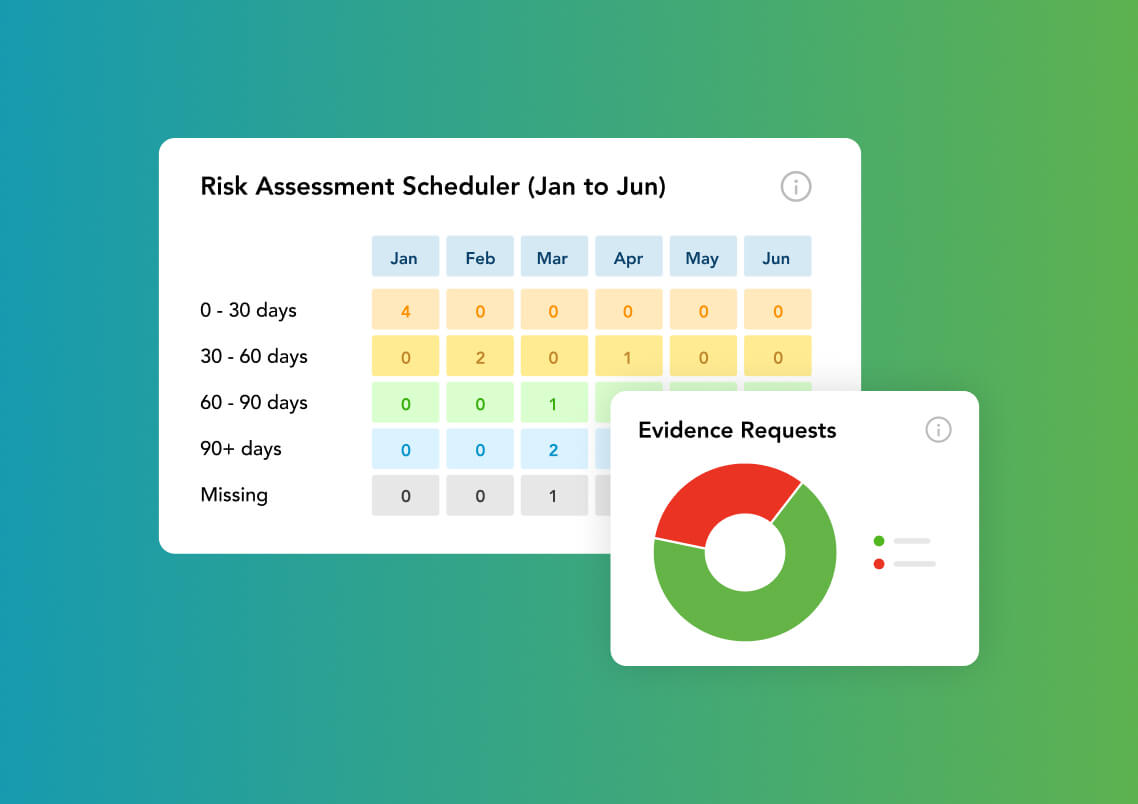
Enterprise Cyber Risk Register
The ProcessUnity enterprise risk register automatically calculates risk ratings based on how you rate severity, likelihood, and impact, then maps risk to mitigating controls and policies. Scheduled risk assessments and evidence requests collect data points for an informed risk analysis throughout the year. As you review the assessment findings, you can create and track action plans to drive immediate improvements where needed.

Cybersecurity Controls Library
ProcessUnity builds your unique control library using a framework mapped to 1,000+ control standards, including NIST Cybersecurity Framework (CSF), NIST 800-53, and ISO 27001. Automated control assessments and evidentiary requests keep your control reviews on schedule, giving you the information necessary to accurately measure control effectiveness (how well the control performs) and maturity (how well the control is implemented).
Smarter Cybersecurity Investments
Doing more with less is hard when all program activities feel critical. ProcessUnity optimizes budget spend by revealing where your investments and peoplepower are most effective across risks, controls, policies, and action plans. By allocating spend effectively, you ensure that cyber investments help mitigate risk and advance security posture. With a detailed report of your current and future budgetary requirements, you can make precise plans for your security roadmap and justify future requests.

Real-Time Cyber Program Reporting
ProcessUnity gives you powerful reporting tools and targeted intelligence to measure and communicate cybersecurity effectiveness. With the click of a button, you gain one-stop visibility into your program performance across risks, controls, policies, action plans, and regulatory requirements. Interactive dashboards provide you with real-time, drill-down insight into the state of enterprise-wide cybersecurity. In seconds, you can generate a custom, board-level report to demonstrate program performance to senior leadership and auditors.

Calculate Your Potential Savings
with ProcessUnity
Build a business case to uplevel your Third-Party Risk Management program. Answer a few short questions and generate your custom savings report.
Calculate Your ROI Now
Frequently Asked Questions
A cybersecurity risk management program is a structured, proactive approach to identifying, assessing, and addressing digital threats to your organization.
Cybersecurity controls are protective measures that safeguard your organization’s information and sensitive data from potential threats. Common examples include firewalls, secure configuration, security update management, user access control, and malware protection.
Cybersecurity controls effectiveness can be measured by continuously monitoring control performance metrics, analyzing the data collected to identify and close security gaps, and tracking improvement against established targets.
The top five cybersecurity risks organizations face today include:
- AI-powered attacks: Threat actors leverage AI to launch more sophisticated, quick, and damaging cyber attacks.
- Third-party vulnerabilities: Inadequate controls and lack of visibility into third parties can leave organizations exposed.
- Insider threats: Employees or contractors with data access may accidentally or deliberately compromise systems and data.
- Ransomware: Attackers encrypt critical data and demand payment, leading to downtime, financial loss, and reputational damage.
- Cloud security gaps: Misconfigurations, insecure APIs, and shared infrastructure increase exposure in cloud environments.
Next Steps:
Schedule a ProcessUnity Platform Demo
Our team is here to show you how forward-thinking organizations are elevating their
Third-Party Risk Management programs and practices to maximize risk reduction. Start
your journey with ProcessUnity today.




