Cybersecurity Performance Management
Cybersecurity Asset Management
In order to build an effective cybersecurity program, it’s essential to monitor and report on the security of your high-value cybersecurity assets. All risks to your assets must be tied to your enterprise controls for true visibility into your organization’s holistic security posture. ProcessUnity Cybersecurity Performance Management (CPM) enables you to map your most important applications and systems to specific control standards and appropriate industry regulations for a comprehensive, up-to-date view of cybersecurity preparedness.

Identify, Track and Mitigate Risks to All
High-Value Assets Under Management
With ProcessUnity CPM, organizations can:
- Track the status of high-value assets, evaluate their impact on the organization’s overall risk posture and determine how to protect them
- Identify and assign asset owners to ensure cybersecurity accountability and understand an asset’s influence on controls
- Map all assets to their associated controls and standards for improved control assuredness and weakness identification
- Automate and schedule ongoing asset assessments for consistent, reliable risk analysis
- Systematize issue creation, tracking and remediation for program visibility and improvements
- Obtain an organization-wide view of all high-value assets under management and their risk impacts to gain insight into the organization’s comprehensive cybersecurity risk posture and control coverage
Catalog and Track Cybersecurity Assets
With a centralized asset database, you can manage your entire asset inventory – applications, systems and facilities – and assign owners to these assets. The register provides the ability to define risk categories and risk families; determine both inherent and residual risk; and then aggregate that risk to groups within the organization.
Map Controls, Standards and Regulations to Assets via the Cybersecurity Control Metaframework
ProcessUnity CPM provides a control metaframework mapped to relevant standards and regulations, including NIST CSF, ISO 27001, GDPR, CMMC and more. This metaframework helps reduce tedious compliance work and adds value by eliminating control duplication across various standards and regulations. As a result, security teams gain assessment clarity and better reporting without a heavy investment of valuable resources.
Streamline Asset Assessments with the ProcessUnity Control Evaluation Engine
Leveraging ProcessUnity Hands-Free Automation™, the Control Evaluation Engine distributes asset reviews to the relevant owner, then scores responses based on company-defined criteria to identify high-value assets. Inherent risk ratings are automatically calculated via the Control Evaluation Engine to help determine assessment cadences and create an asset assessment schedule. Periodic assessments enable cybersecurity teams to identify control gaps or risk trends across the organization’s entire asset population. As a result, teams gain clarity on where to implement protective security controls to address organizational vulnerabilities that stem from their assets’ exposures to risk.
Leverage the Issue Remediation Suite for Security Enhancements
The ProcessUnity Issue Remediation Suite reduces the time it takes to create, track and remediate issues while reducing subjectivity by systematizing the issue creation process. ProcessUnity CPM provides a one-stop-shop for managing these issues and their remediation plans. Issues can be described and categorized with severity ratings; and appropriate personnel can be notified to take necessary actions. Real-time reporting provides a birds-eye view of issue statuses that can be used to identify systemic problems within your organization. In-depth issue tracking allows you to track open issues to resolution, ensuring that project components stay on schedule.
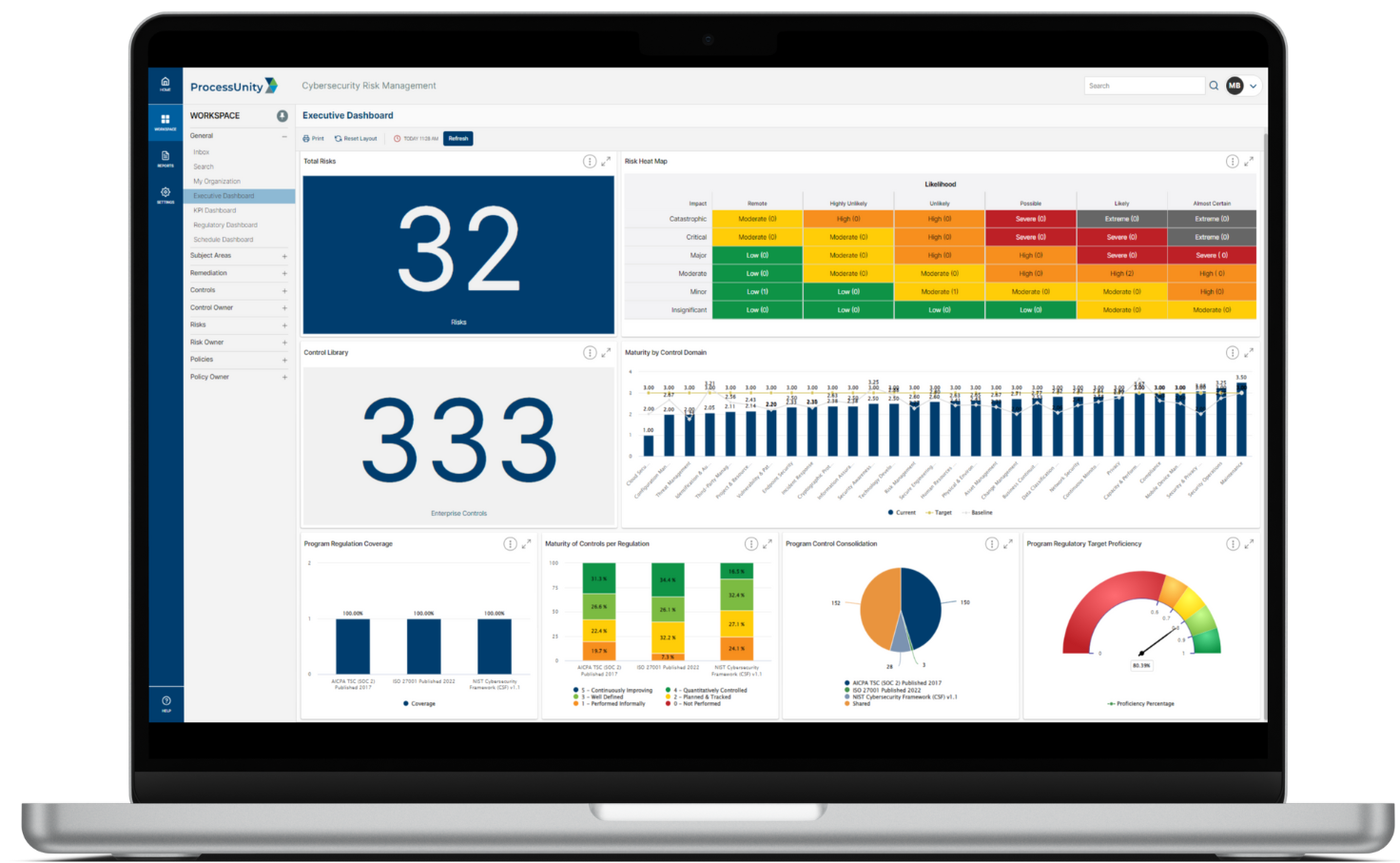
Gain Asset Insight via the Cybersecurity Performance Command Center
The ProcessUnity Cybersecurity Performance Command Center enables you to execute risk mitigation and security improvement activities across your high-value assets. With a complete, real-time view of your organization’s high-value assets, you gain critical insight into all risks, issues, projects and controls facing an asset. Drill-down capabilities in performance dashboards allow you to quickly explore the details in any areas of concern, while extensive custom reporting capabilities enable the creation of role-specific reports. These reports demonstrate to executives and regulators the existence of a consistent, reliable process for managing your assets.
Beyond understanding the risk factor of each asset, reports also help your cybersecurity teams identify themes across asset categories. This feature helps you to identify critical control weaknesses that merit remediation projects to protect your assets.
Request a Demo: ProcessUnity's Cybersecurity Risk Management Platform
Hundreds of organizations worldwide rely on ProcessUnity Cybersecurity Risk Management to implement a centralized system of record for managing cybersecurity activities across the organization. Contact us to start your journey today!
Request a Demo: ProcessUnity's Cybersecurity Risk Management Platform