Cybersecurity Performance Management
Cybersecurity Governance
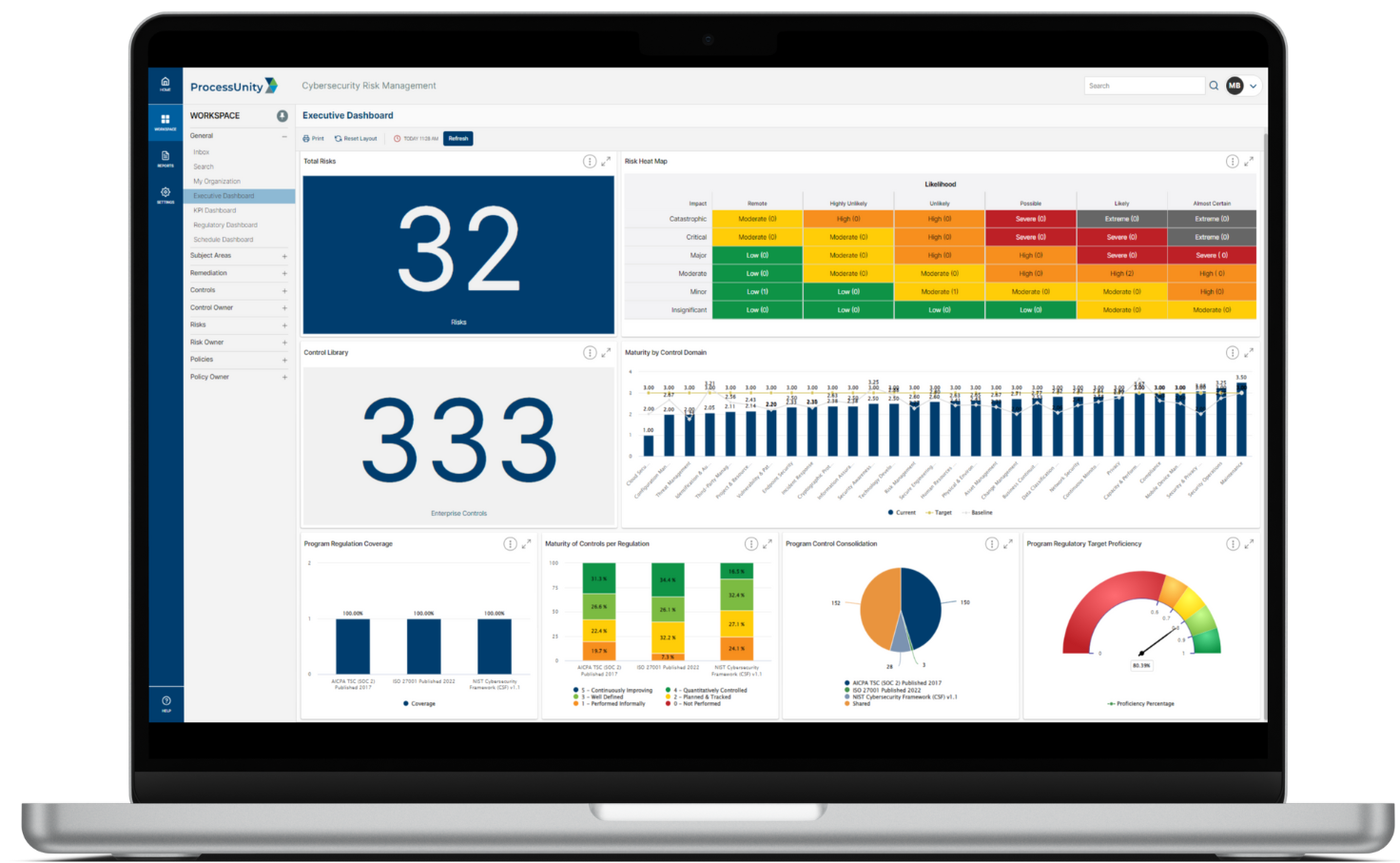
While threats, risks and high-value assets often take priority for cybersecurity programs, your organization must promote enterprise-wide security accountability to stay resilient. Employee awareness and training programs, policies and procedures and user access are all areas that impact the performance rating of enterprise controls. Your team needs to verify that employees support your cybersecurity priorities by upholding all policies and procedures. ProcessUnity Cybersecurity Performance Management (CPM) enables comprehensive oversight of your organizational security by mapping your critical program components to relevant controls and identifying gaps in your internal policies.
Gain Control and Maintain Oversight Over Policies, Procedures, Employee Training and Access
With the ProcessUnity CPM Cybersecurity Governance capabilities, organizations:
- Align policies and procedures with controls, regulations and standards to identify and remediate gaps
- Gain oversight of employee training programs and automate attestation activity
- Maintain an updated, reusable database for all client due diligence requests
- Centralize user access information and drive user access review activities
Gain Visibility Across Policies, Procedures and Controls with the Cybersecurity Control Metaframework
At many organizations, security leaders have fragmented information on the status of the controls, processes, policies and procedures. They’re in the dark about the effectiveness of these processes and controls, unaware of existing gaps that need attention.
ProcessUnity CPM catalogs and maps internal policies to controls, automating a consistent review process across your policies, procedures and user access. The platform identifies weaknesses based on company-defined criteria, driving any associated issues through to mitigation.
Ensure Employees Support All Relevant Policies and Procedures
You need assurance that your cybersecurity policies are implemented throughout your organization. Periodic employee training and acknowledgment activities must be conducted to verify that employees are compliant with all internal policies. With ProcessUnity CPM, assessments and questionnaires can be automatically sent on a predetermined schedule. Built-in tracking and escalation drive activities to conclusion and provide the documentation needed for any audit activity.
Maintain a Response Database to Streamline Due Diligence Requests
While due diligence requests are a necessary cost of doing business, maintaining a current and reusable database for all client due diligence requests can ease this burden. With ProcessUnity CPM, organizations can organize, store and search a library of cybersecurity due diligence responses to expedite client assurance activities. A central repository of gold-master responses and supporting evidence helps you spend less time on completing repetitive questionnaires.
Automate Policy Reviews and Manage User Access Controls via the ProcessUnity Control Evaluation Engine
Maintaining control of your systems, applications and programs that employees can access is critical for keeping a pulse on security. The ProcessUnity Control Evaluation Engine automatically distributes assessments to the relevant stakeholders to determine adequate access levels for employees, teams and contractors. ProcessUnity CPM documents these access levels, automates policy review schedules, pushes the notifications and escalation routing necessary to ensure completion, all while tracking the entire process to document compliance.
Request a Demo: ProcessUnity's Cybersecurity Risk Management Platform
Hundreds of organizations worldwide rely on ProcessUnity Cybersecurity Risk Management to implement a centralized system of record for managing cybersecurity activities across the organization. Contact us to start your journey today!
Request a Demo: ProcessUnity's Cybersecurity Risk Management Platform